1.
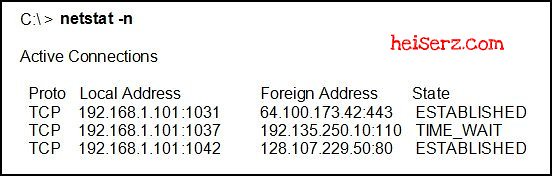
Refer to the exhibit. What two pieces of information can be determined from the output that is shown? (Choose two.)
The local host is using three client sessions.The local host is using web sessions to a remote server.The local host is listening for TCP connections using public addresses.
The local host is using well-known port numbers to identify the source ports.
The local host is performing the three-way handshake with 192.168.1.101:1037.
2. After a web browser makes a request to a web server that is listening to the standard port, what will be the source port number in the TCP header of the response from the server?
13
53
801024
1728
13
53
801024
1728
3. Which information is found in both the TCP and UDP header information?
sequencing
flow control
acknowledgments
source and destination
sequencing
flow control
acknowledgments
source and destination
4. Which is an important characteristic of UDP?
acknowledgement of data delivery
minimal delays in data deliveryhigh reliability of data delivery
same order data delivery
acknowledgement of data delivery
minimal delays in data deliveryhigh reliability of data delivery
same order data delivery
5.
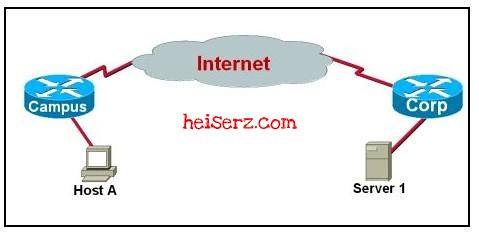
Refer to the exhibit. Host A is using FTP to download a large file from Server 1. During the download process, Server 1 does not receive an acknowledgment from Host A for several bytes of transferred data. What action will Server 1 take as a result?
create a Layer 1 jam signal
reach a timeout and resend the data that needs to be acknowledgedsend a RESET bit to the host
change the window size in the Layer 4 header

Refer to the exhibit. Host A is using FTP to download a large file from Server 1. During the download process, Server 1 does not receive an acknowledgment from Host A for several bytes of transferred data. What action will Server 1 take as a result?
create a Layer 1 jam signal
reach a timeout and resend the data that needs to be acknowledgedsend a RESET bit to the host
change the window size in the Layer 4 header
6.
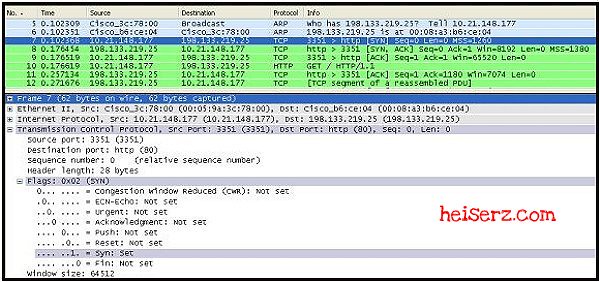
Refer to the exhibit. In line 7 of this Wireshark capture, what TCP operation is being performed?
session establishmentsegment retransmit
data transfer
session disconnect

Refer to the exhibit. In line 7 of this Wireshark capture, what TCP operation is being performed?
session establishmentsegment retransmit
data transfer
session disconnect
7.
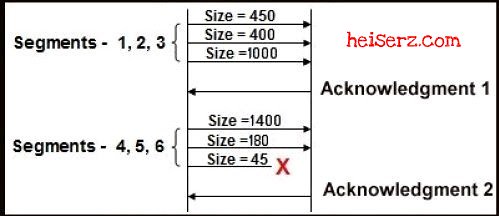
Refer to the exhibit. The initial TCP exchange of data between two hosts is shown in the exhibit. Assuming an initial sequence number of 0, what sequence number will be included in Acknowledgment 2 if Segment 6 is lost?
2
3
6
1850
34313475

Refer to the exhibit. The initial TCP exchange of data between two hosts is shown in the exhibit. Assuming an initial sequence number of 0, what sequence number will be included in Acknowledgment 2 if Segment 6 is lost?
2
3
6
1850
34313475
8. Why is flow control used for TCP data transfer?
to synchronize equipment speed for sent data
to synchronize and order sequence numbers so data is sent in complete numerical order
to prevent the receiver from being overwhelmed by incoming datato synchronize window size on the server
to simplify data transfer to multiple hosts
to synchronize equipment speed for sent data
to synchronize and order sequence numbers so data is sent in complete numerical order
to prevent the receiver from being overwhelmed by incoming datato synchronize window size on the server
to simplify data transfer to multiple hosts
9. During a TCP communication session, if the packets arrive to the destination out of order, what will happen to the original message?
The packets will not be delivered.
The packets will be retransmitted from the source.
The packets will be delivered and reassembled at the destination.The packets will be delivered and not reassembled at the destination.
The packets will not be delivered.
The packets will be retransmitted from the source.
The packets will be delivered and reassembled at the destination.The packets will be delivered and not reassembled at the destination.
10. With TCP/IP data encapsulation, which range of port numbers identifies all well-known applications?
0 to 255
256 to 1022
0 to 10231024 to 2047
49153 to 65535
0 to 255
256 to 1022
0 to 10231024 to 2047
49153 to 65535
11. Which transport layer protocol provides low overhead and would be used for applications which do not require reliable data delivery?
TCP
IP
UDPHTTP
DNS
TCP
IP
UDPHTTP
DNS
12. What are two features of the User Datagram Protocol (UDP)? (Choose two.)
flow control
low overheadconnectionlessconnection-oriented
sequence and acknowledgements
flow control
low overheadconnectionlessconnection-oriented
sequence and acknowledgements
13. What mechanism is used by TCP to provide flow control as segments travel from source to destination?
sequence numbers
session establishment
window sizeacknowledgments
sequence numbers
session establishment
window sizeacknowledgments
14. What is dynamically selected by the source host when forwarding data?
destination logical address
source physical address
default gateway address
source port
destination logical address
source physical address
default gateway address
source port
15. Why are port numbers included in the TCP header of a segment?
to indicate the correct router interface that should be used to forward a segment
to identify which switch ports should receive or forward the segment
to determine which Layer 3 protocol should be used to encapsulate the data
to enable a receiving host to forward the data to the appropriate applicationto allow the receiving host to assemble the packet in the proper order
to indicate the correct router interface that should be used to forward a segment
to identify which switch ports should receive or forward the segment
to determine which Layer 3 protocol should be used to encapsulate the data
to enable a receiving host to forward the data to the appropriate applicationto allow the receiving host to assemble the packet in the proper order
16. Which two options represent Layer 4 addressing? (Choose two.)
identifies the destination network
identifies source and destination hosts
identifies the communicating applicationsidentifies multiple conversations between the hostsidentifies the devices communicating over the local media
identifies the destination network
identifies source and destination hosts
identifies the communicating applicationsidentifies multiple conversations between the hostsidentifies the devices communicating over the local media
17. Which three features allow TCP to reliably and accurately track the transmission of data from source to destination?
encapsulation
flow controlconnectionless services
session establishmentnumbering and sequencingbest effort delivery
encapsulation
flow controlconnectionless services
session establishmentnumbering and sequencingbest effort delivery
18. Which OSI model layer is responsible for regulating the flow of information from source to destination, reliably and accurately?
application
presentation
session
transportnetwork
application
presentation
session
transportnetwork
19.
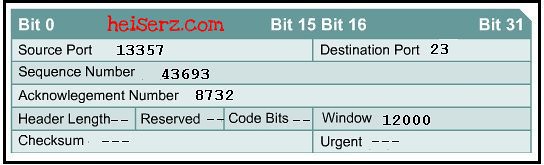
Based on the transport layer header shown in the diagram, which of the following statements describe the established session? (Choose two.)
This is a UDP header.
This contains a Telnet request.This contains a TFTP data transfer.
The return packet from this remote host will have an Acknowledgement Number of 43693.
This is a TCP header.

Based on the transport layer header shown in the diagram, which of the following statements describe the established session? (Choose two.)
This is a UDP header.
This contains a Telnet request.This contains a TFTP data transfer.
The return packet from this remote host will have an Acknowledgement Number of 43693.
This is a TCP header.
20. Which event occurs during the transport layer three-way handshake?
The two applications exchange data.
TCP initializes the sequence numbers for the sessions.UDP establishes the maximum number of bytes to be sent.
The server acknowledges the bytes of data received from the client.
The two applications exchange data.
TCP initializes the sequence numbers for the sessions.UDP establishes the maximum number of bytes to be sent.
The server acknowledges the bytes of data received from the client.
21.
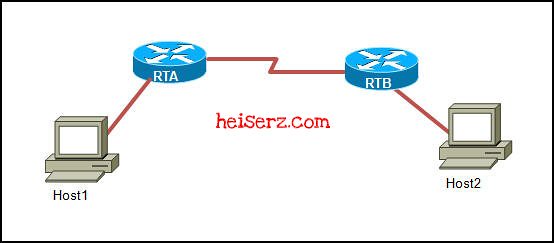
Refer to the exhibit. Host1 is in the process of setting up a TCP session with Host2. Host1 has sent a SYN message to begin session establishment. What happens next?
Host1 sends a segment with the ACK flag = 0, SYN flag = 0 to Host2.
Host1 sends a segment with the ACK flag = 1, SYN flag = 0 to Host2.
Host1 sends a segment with the ACK flag = 1, SYN flag = 1 to Host2.
Host2 sends a segment with the ACK flag = 0, SYN flag = 1 to Host1.
Host2 sends a segment with the ACK flag = 1, SYN flag = 0 to Host1.
Host2 sends a segment with the ACK flag = 1, SYN flag = 1 to Host1.

Refer to the exhibit. Host1 is in the process of setting up a TCP session with Host2. Host1 has sent a SYN message to begin session establishment. What happens next?
Host1 sends a segment with the ACK flag = 0, SYN flag = 0 to Host2.
Host1 sends a segment with the ACK flag = 1, SYN flag = 0 to Host2.
Host1 sends a segment with the ACK flag = 1, SYN flag = 1 to Host2.
Host2 sends a segment with the ACK flag = 0, SYN flag = 1 to Host1.
Host2 sends a segment with the ACK flag = 1, SYN flag = 0 to Host1.
Host2 sends a segment with the ACK flag = 1, SYN flag = 1 to Host1.