1. One switch in a Layer 2 switched spanning-tree domain is converted to PVRST+ using the spanning-tree mode rapid-pvst global configuration mode command. The remaining switches are running PVST+. What is the effect on the spanning-tree operation?
Spanning tree is effectively disabled in the network.
The PVRST+ switch forwards 802.1D BPDUs, but does not participate as a node in any spanning tree.
All switches default to one 802.1D spanning tree for all VLANs.
The PVSRT+ reverts to PVST+ to interoperate with the PVST+ switches.
The PVRST+ switch forwards 802.1D BPDUs, but does not participate as a node in any spanning tree.
All switches default to one 802.1D spanning tree for all VLANs.
The PVSRT+ reverts to PVST+ to interoperate with the PVST+ switches.
2.
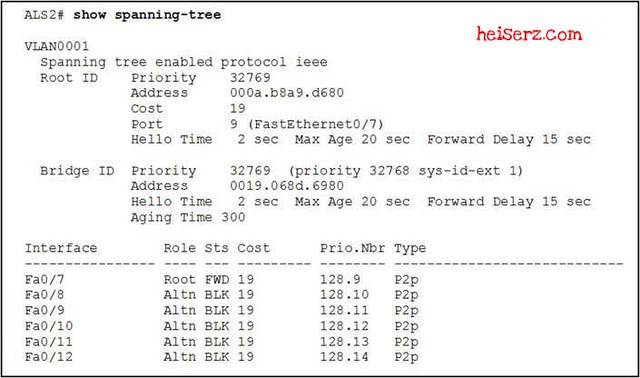
Refer to the exhibit. What implementation of spanning tree best describes the spanning-tree operational mode of the switch?
IEEE 802.1D
IEEE 802.w
IEEE 802.1s
PVRST+

Refer to the exhibit. What implementation of spanning tree best describes the spanning-tree operational mode of the switch?
IEEE 802.1D
IEEE 802.w
IEEE 802.1s
PVRST+
3.
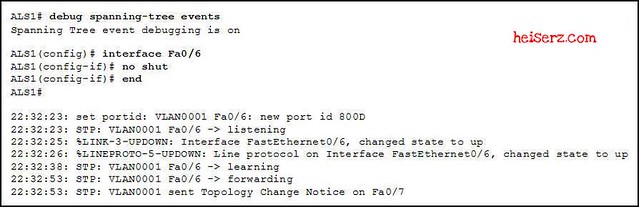
Refer to the exhibit. What conclusion does the output support?
PortFast is enabled on interface Fa0/6.
IEEE 802.1w is enabled on VLAN 1.
The forward delay timer has been changed from the default value.
Standard IEEE 802.1D behavior is shown.

Refer to the exhibit. What conclusion does the output support?
PortFast is enabled on interface Fa0/6.
IEEE 802.1w is enabled on VLAN 1.
The forward delay timer has been changed from the default value.
Standard IEEE 802.1D behavior is shown.
4.
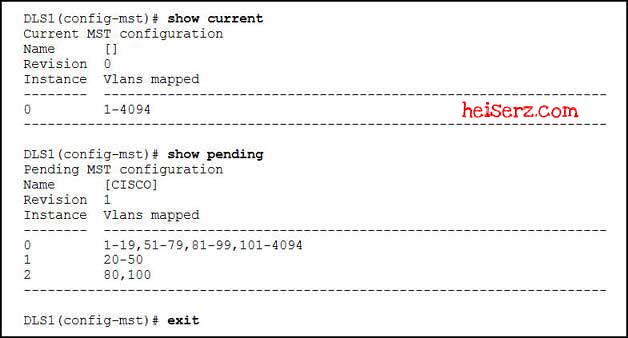
Refer to the exhibit. After the sequence of commands is entered, how many VLANs will be assigned to the default instance?
4094
4064
4062
4061

Refer to the exhibit. After the sequence of commands is entered, how many VLANs will be assigned to the default instance?
4094
4064
4062
4061
5.
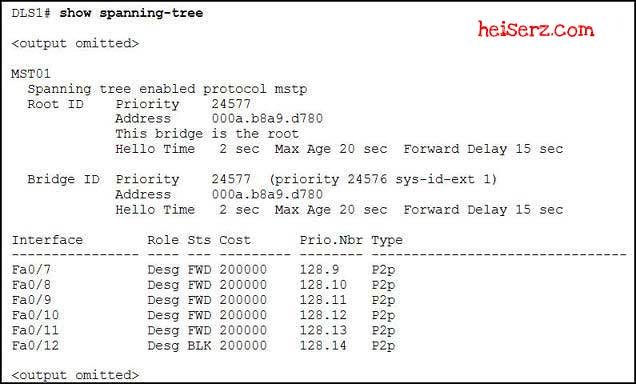
Refer to the exhibit. What two conclusions does the output show to be true? (Choose two.)
DLS1 is running IEEE 802.1s on instance 1.
DLS1 is running IEEE 802.1D on instance 1.
DLS1 is the root bridge for instance 1.
Interface Fa0/12 will move into the errdisable state if a BPDU is received.
Interfaces Fa0/1 through Fa0/6 are trunk ports.

Refer to the exhibit. What two conclusions does the output show to be true? (Choose two.)
DLS1 is running IEEE 802.1s on instance 1.
DLS1 is running IEEE 802.1D on instance 1.
DLS1 is the root bridge for instance 1.
Interface Fa0/12 will move into the errdisable state if a BPDU is received.
Interfaces Fa0/1 through Fa0/6 are trunk ports.
6. Which three parameters should match all switches within an MST region? (Choose three.)
port costs on trunk ports
configuration name
revision number
trunk encapsulation method
bridge priority
VLAN-to-instance mappings
port costs on trunk ports
configuration name
revision number
trunk encapsulation method
bridge priority
VLAN-to-instance mappings
7. Users complain that they lost connectivity to all resources in the network. A network administrator suspects the presence of a bridging loop as a root cause of the problem. Which two actions will determine the existence of the bridging loop? (Choose two.)
Confirm MAC port security is enabled on all access switches.
Check the port utilization on devices and look for abnormal values.
Verify that the management VLAN is properly configured on all root bridges.
Capture the traffic on the saturated link and verify if duplicate packets are seen.
Ensure that the root guard and loop guard are properly configured on all distribution links.
Confirm MAC port security is enabled on all access switches.
Check the port utilization on devices and look for abnormal values.
Verify that the management VLAN is properly configured on all root bridges.
Capture the traffic on the saturated link and verify if duplicate packets are seen.
Ensure that the root guard and loop guard are properly configured on all distribution links.
8.
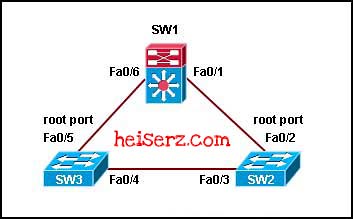
Refer to the exhibit. Switch SW1 is receiving traffic from SW2. However, SW2 is not receiving traffic from SW1. Which STP feature should be implemented to prevent inadvertent loops in the network?
UDLD
PortFast
BPDU guard
BPDU filtering

Refer to the exhibit. Switch SW1 is receiving traffic from SW2. However, SW2 is not receiving traffic from SW1. Which STP feature should be implemented to prevent inadvertent loops in the network?
UDLD
PortFast
BPDU guard
BPDU filtering
9. Which interfaces should loop guard be enabled on?
root ports
designated ports
root port and alternate ports
ports configured with PortFast
root port and ports configured with PortFast
root ports
designated ports
root port and alternate ports
ports configured with PortFast
root port and ports configured with PortFast
10. What will happen when a BPDU is received on a loop guard port that is in a loop-inconsistent state?
The port will transition to blocking state.
The port will transition to forwarding state automatically.
The port will be disabled and the administrator must re-enable it manually.
The port will transition to the appropriate state as determined by the normal function of the spanning tree.
The port will transition to blocking state.
The port will transition to forwarding state automatically.
The port will be disabled and the administrator must re-enable it manually.
The port will transition to the appropriate state as determined by the normal function of the spanning tree.
11.
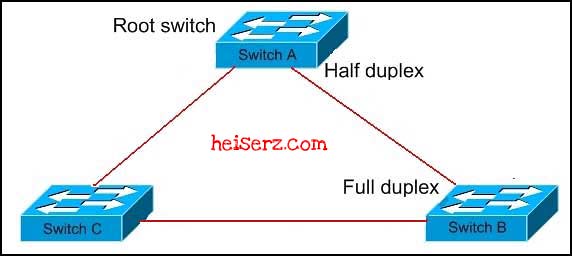
Refer to the exhibit. STP is enabled on all switches in the network. The port on switch A that connects to switch B is half duplex. The port on switch B that connects to switch A is full duplex. What are three problems that this scenario could create? (Choose three.)
Switch B will become the root switch.
Switch B may unblock its port to switch C, thereby creating a loop.
Switch A is performing carrier sense and collision detection, and switch B is not.
Autonegotiation results in both switch A and switch B failing to perform carrier sense.
BPDUs may not successfully negotiate port states on the link between switch A and switch B.
Spanning tree will keep re-calculating, thereby consuming all the CPU normally used for traffic.

Refer to the exhibit. STP is enabled on all switches in the network. The port on switch A that connects to switch B is half duplex. The port on switch B that connects to switch A is full duplex. What are three problems that this scenario could create? (Choose three.)
Switch B will become the root switch.
Switch B may unblock its port to switch C, thereby creating a loop.
Switch A is performing carrier sense and collision detection, and switch B is not.
Autonegotiation results in both switch A and switch B failing to perform carrier sense.
BPDUs may not successfully negotiate port states on the link between switch A and switch B.
Spanning tree will keep re-calculating, thereby consuming all the CPU normally used for traffic.
12.
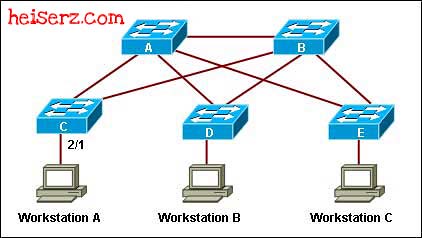
Refer to the exhibit. STP is configured on all switches in the network. Recently, the user on workstation A lost connectivity to the rest of the network. At the same time, the administrator received the console message:

Refer to the exhibit. STP is configured on all switches in the network. Recently, the user on workstation A lost connectivity to the rest of the network. At the same time, the administrator received the console message:
%SPANTREE-2-RX_PORTFAST:Received BPDU on PortFast enable port.Disabling 2/1
What is the cause of the problem?
STP PortFast feature has been disabled on port 2/1.
STP PortFast feature has been enabled on port 2/1.
PAgP has removed port 2/1 from the EtherChannel bundle.
The STP PortFast BPDU Guard feature has disabled port 2/1 on the switch.
STP PortFast feature has been disabled on port 2/1.
STP PortFast feature has been enabled on port 2/1.
PAgP has removed port 2/1 from the EtherChannel bundle.
The STP PortFast BPDU Guard feature has disabled port 2/1 on the switch.
13. What are three important steps in troubleshooting STP problems? (Choose three.)
Administratively create bridge loops and see what path the traffic takes.
Administratively disable multicasting and check to see if connectivity is restored.
Check each side of a point-to-point link for duplex mismatch.
Adjust BPDU timers so that there is less overhead traffic on the switching fabric.
Administratively disable ports that should be blocking and check to see if connectivity is restored.
Capture traffic on a saturated link and check whether identical frames are traversing multiple links.
Administratively create bridge loops and see what path the traffic takes.
Administratively disable multicasting and check to see if connectivity is restored.
Check each side of a point-to-point link for duplex mismatch.
Adjust BPDU timers so that there is less overhead traffic on the switching fabric.
Administratively disable ports that should be blocking and check to see if connectivity is restored.
Capture traffic on a saturated link and check whether identical frames are traversing multiple links.
14. Which statement is true about UDLD?
It is automatically enabled.
It allows devices to transmit traffic one way.
It will disable an EtherChannel bundle if one link has failed.
It allows a switch to detect a unidirectional link and shut down the affected interface.
It is automatically enabled.
It allows devices to transmit traffic one way.
It will disable an EtherChannel bundle if one link has failed.
It allows a switch to detect a unidirectional link and shut down the affected interface.
15. Which two statements are true about STP root guard? (Choose two.)
Root guard is enabled on a per-port basis.
Root guard requires that PortFast be enabled on a switch port.
Root guard re-enables a switch port once it stops receiving superior BPDUs.
Root guard should be configured on all ports on the desired root bridge to prevent another bridge from becoming the root.
If a root guard enabled port receives a inferior BPDU from a nonroot switch, the port transitions to the blocking state to prevent a root bridge election.
Root guard is enabled on a per-port basis.
Root guard requires that PortFast be enabled on a switch port.
Root guard re-enables a switch port once it stops receiving superior BPDUs.
Root guard should be configured on all ports on the desired root bridge to prevent another bridge from becoming the root.
If a root guard enabled port receives a inferior BPDU from a nonroot switch, the port transitions to the blocking state to prevent a root bridge election.
16. What happens when a switch running IEEE 802.1D receives a topology change message from the root bridge?
The switch uses the forward delay timer to age out entries in the MAC address table.
The switch uses the max-age timer to age out entries in the MAC address table.
The switch uses the hello to age out entries in the MAC address table.
The switch uses the forward delay and the max-age timer to age out entries in the MAC address table.
The switch uses the forward delay timer to age out entries in the MAC address table.
The switch uses the max-age timer to age out entries in the MAC address table.
The switch uses the hello to age out entries in the MAC address table.
The switch uses the forward delay and the max-age timer to age out entries in the MAC address table.
17. Which STP timer defines the length of time spent in the listening and learning states?
hello time
forward aging
forward delay
max age
max delay
hello time
forward aging
forward delay
max age
max delay
18. Which three statements about RSTP are true? (Choose three.)
An RSTP BPDU carries information about port roles and is sent to neighbor switches only.
RSTP elects a root bridge in exactly the same way as 802.1D.
RSTP is capable of reverting back to 802.1D but still maintains the benefits of 802.1w.
RSTP is recognized as the IEEE 802.1w standard.
There are only three RSTP port states: discarding, listening, and forwarding.
UplinkFast and BackboneFast are compatible with RSTP.
An RSTP BPDU carries information about port roles and is sent to neighbor switches only.
RSTP elects a root bridge in exactly the same way as 802.1D.
RSTP is capable of reverting back to 802.1D but still maintains the benefits of 802.1w.
RSTP is recognized as the IEEE 802.1w standard.
There are only three RSTP port states: discarding, listening, and forwarding.
UplinkFast and BackboneFast are compatible with RSTP.
19. Which protocol extends the IEEE 802.1w Rapid Spanning Tree (RST) algorithm to multiple spanning trees?
STP
RSTP+
CST
MST
STP
RSTP+
CST
MST
20. Which protocol should an administrator recommend to manage bridged links when the customer requires a fully redundant network that can utilize load balancing technologies and reconverge on link failures in less than a second?
IEEE 802.1Q (CST)
IEEE 802.1s (MST)
Cisco PVST+
IEEE 802.1D(STP)
IEEE 802.1Q (CST)
IEEE 802.1s (MST)
Cisco PVST+
IEEE 802.1D(STP)
21. Refer to the exhibit. How far is a broadcast frame that is sent by computer A propagated in the LAN domain?
none of the computers will receive the broadcast frame
computer A, computer B, computer C
computer A, computer D, computer G
computer B, computer C
computer D, computer G
computer A, computer B, computer C, computer D, computer E, computer F, computer G, computer H, computer I
none of the computers will receive the broadcast frame
computer A, computer B, computer C
computer A, computer D, computer G
computer B, computer C
computer D, computer G
computer A, computer B, computer C, computer D, computer E, computer F, computer G, computer H, computer I
22. The network administrator wants to separate hosts in Building A into two VLANs numbered 20 and 30. Which two statements are true concerning VLAN configuration? (Choose two.)
The VLANs may be named.
VLAN information is saved in the startup configuration.
Non-default VLANs created manually must use the extended range VLAN numbers.
The network administrator may create the VLANs in either global configuration mode or VLAN database mode.
Both VLANs may be named BUILDING_A to distinguish them from other VLANs in different geographical locations.
The VLANs may be named.
VLAN information is saved in the startup configuration.
Non-default VLANs created manually must use the extended range VLAN numbers.
The network administrator may create the VLANs in either global configuration mode or VLAN database mode.
Both VLANs may be named BUILDING_A to distinguish them from other VLANs in different geographical locations.
23. Refer to the exhibit. Which statement is true concerning interface Fa0/5?
The default native VLAN is being used.
The trunking mode is set to auto.
Trunking can occur with non-Cisco switches.
VLAN information about the interface encapsulates the Ethernet frames.
The default native VLAN is being used.
The trunking mode is set to auto.
Trunking can occur with non-Cisco switches.
VLAN information about the interface encapsulates the Ethernet frames.
24. Refer to the exhibit. Computer 1 sends a frame to computer 4. On which links along the path between computer 1 and computer 4 will a VLAN ID tag be included with the frame?
A
A, B
A, B, D, G
A, D, F
C, E
C, E, F
A
A, B
A, B, D, G
A, D, F
C, E
C, E, F
25. Refer to the exhibit. SW1 and SW2 are new switches being installed in the topology shown in the exhibit. Interface Fa0/1 on switch SW1 has been configured with trunk mode “on”. Which statement is true about forming a trunk link between the switches SW1 and SW2?
Interface Fa0/2 on switch SW2 will negotiate to become a trunk link if it supports DTP.
Interface Fa0/2 on switch SW2 can only become a trunk link if statically configured as a trunk.
Interface Fa0/1 converts the neighboring link on the adjacent switch into a trunk link if the neighboring interface is configured in nonegotiate mode.
Interface Fa0/1 converts the neighboring link on the adjacent switch into a trunk link automatically with no consideration of the configuration on the neighboring interface.
Interface Fa0/2 on switch SW2 will negotiate to become a trunk link if it supports DTP.
Interface Fa0/2 on switch SW2 can only become a trunk link if statically configured as a trunk.
Interface Fa0/1 converts the neighboring link on the adjacent switch into a trunk link if the neighboring interface is configured in nonegotiate mode.
Interface Fa0/1 converts the neighboring link on the adjacent switch into a trunk link automatically with no consideration of the configuration on the neighboring interface.
26. Which statement describes how hosts on VLANs communicate?
Hosts on different VLANs use VTP to negotiate a trunk.
Hosts on different VLANs communicate through routers.
Hosts on different VLANs should be in the same IP network.
Hosts on different VLANs examine VLAN ID in the frame tagging to determine if the frame for their network.
Hosts on different VLANs use VTP to negotiate a trunk.
Hosts on different VLANs communicate through routers.
Hosts on different VLANs should be in the same IP network.
Hosts on different VLANs examine VLAN ID in the frame tagging to determine if the frame for their network.
27. Which two statements describe the benefits of VLANs? (Choose two.)
VLANs improve network performance by regulating flow control and window size.
VLANs enable switches to route packets to remote networks via VLAN ID filtering.
VLANs reduce network cost by reducing the number of physical ports required on switches.
VLANs improve network security by isolating users that have access to sensitive data and applications.
VLANs divide a network into smaller logical networks, resulting in lower susceptibility to broadcast storms.
VLANs improve network performance by regulating flow control and window size.
VLANs enable switches to route packets to remote networks via VLAN ID filtering.
VLANs reduce network cost by reducing the number of physical ports required on switches.
VLANs improve network security by isolating users that have access to sensitive data and applications.
VLANs divide a network into smaller logical networks, resulting in lower susceptibility to broadcast storms.
28. A network administrator is removing several VLANs from a switch. When the administrator enters the no vlan 1 command, an error is received. Why did this command generate an error?
VLAN 1 can never be deleted.
VLAN 1 can only be deleted by deleting the vlan.dat file.
VLAN 1 can not be deleted until all ports have been removed from it.
VLAN 1 can not be deleted until another VLAN has been assigned its responsibilities.
VLAN 1 can never be deleted.
VLAN 1 can only be deleted by deleting the vlan.dat file.
VLAN 1 can not be deleted until all ports have been removed from it.
VLAN 1 can not be deleted until another VLAN has been assigned its responsibilities.
29. What is the effect of the switchport mode dynamic desirable command?
DTP cannot negotiate the trunk since the native VLAN is not the default VLAN.
The remote connected interface cannot negotiate a trunk unless it is also configured as dynamic desirable.
The connected devices dynamically determine when data for multiple VLANs must be transmitted across the link and bring the trunk up as needed.
A trunk link is formed if the remote connected device is configured with the switchport mode dynamic auto or switchport mode trunk commands.
DTP cannot negotiate the trunk since the native VLAN is not the default VLAN.
The remote connected interface cannot negotiate a trunk unless it is also configured as dynamic desirable.
The connected devices dynamically determine when data for multiple VLANs must be transmitted across the link and bring the trunk up as needed.
A trunk link is formed if the remote connected device is configured with the switchport mode dynamic auto or switchport mode trunk commands.
30. What is a valid consideration for planning VLAN traffic across multiple switches?
Configuring interswitch connections as trunks will cause all hosts on any VLAN to receive broadcasts from the other VLANs.
A trunk connection is affected by broadcast storms on any particular VLAN that is carried by that trunk.
Restricting trunk connections between switches to a single VLAN will improve efficiency of port usage.
Carrying all required VLANs on a single access port will ensure proper traffic separation.
Configuring interswitch connections as trunks will cause all hosts on any VLAN to receive broadcasts from the other VLANs.
A trunk connection is affected by broadcast storms on any particular VLAN that is carried by that trunk.
Restricting trunk connections between switches to a single VLAN will improve efficiency of port usage.
Carrying all required VLANs on a single access port will ensure proper traffic separation.
31. Refer to the exhibit. The exhibited configurations do not allow the switches to form a trunk. What is the most likely cause of this problem?
Cisco switches only support the ISL trunking protocol.
The trunk cannot be negotiated with both ends set to auto.
By default, Switch1 will only allow VLAN 5 across the link.
A common native VLAN should have been configured on the switches.
Cisco switches only support the ISL trunking protocol.
The trunk cannot be negotiated with both ends set to auto.
By default, Switch1 will only allow VLAN 5 across the link.
A common native VLAN should have been configured on the switches.
32. Refer to the exhibit. Which two conclusions can be drawn regarding the switch that produced the output shown? (Choose two.)
The network administrator configured VLANs 1002-1005.
The VLANs are in the active state and are in the process of negotiating configuration parameters.
A FDDI trunk has been configured on this switch.
The command switchport access vlan 20 was entered in interface configuration mode for Fast Ethernet interface 0/1.
Devices attached to ports fa0/5 through fa0/8 cannot communicate with devices attached to ports fa0/9 through fa0/12 without the use of a Layer 3 device.
The network administrator configured VLANs 1002-1005.
The VLANs are in the active state and are in the process of negotiating configuration parameters.
A FDDI trunk has been configured on this switch.
The command switchport access vlan 20 was entered in interface configuration mode for Fast Ethernet interface 0/1.
Devices attached to ports fa0/5 through fa0/8 cannot communicate with devices attached to ports fa0/9 through fa0/12 without the use of a Layer 3 device.
33. Switch port fa0/1 was manually configured as a trunk, but now it will be used to connect a host to the network. How should the network administrator reconfigure switch port Fa0/1?
Disable DTP.
Delete any VLANs currently being trunked through port Fa0/1.
Administratively shut down and re-enable the interface to return it to default.
Enter the switchport mode access command in interface configuration mode.
Disable DTP.
Delete any VLANs currently being trunked through port Fa0/1.
Administratively shut down and re-enable the interface to return it to default.
Enter the switchport mode access command in interface configuration mode.
34. What are two characteristics of VLAN1 in a default switch configuration? (Choose two.)
VLAN1 should renamed.
VLAN 1 is the management VLAN.
All switch ports are members of VLAN1.
Only switch port 0/1 is assigned to VLAN1.
Links between switches must be members of VLAN1.
VLAN1 should renamed.
VLAN 1 is the management VLAN.
All switch ports are members of VLAN1.
Only switch port 0/1 is assigned to VLAN1.
Links between switches must be members of VLAN1.
35. What switch port modes will allow a switch to successfully form a trunking link if the neighboring switch port is in “dynamic desirable” mode?
dynamic desirable mode
on or dynamic desirable mode
on, auto, or dynamic desirable mode
on, auto, dynamic desirable, or nonegotiate mode
dynamic desirable mode
on or dynamic desirable mode
on, auto, or dynamic desirable mode
on, auto, dynamic desirable, or nonegotiate mode
36. What statement about the 802.1q trunking protocol is true?
802.1q is Cisco proprietary.
802.1q frames are mapped to VLANs by MAC address.
802.1q does NOT require the FCS of the original frame to be recalculated.
802.1q will not perform operations on frames that are forwarded out access ports.
802.1q is Cisco proprietary.
802.1q frames are mapped to VLANs by MAC address.
802.1q does NOT require the FCS of the original frame to be recalculated.
802.1q will not perform operations on frames that are forwarded out access ports.
37. Refer to the exhibit. The network administrator has just added VLAN 50 to Switch1 and Switch2 and assigned hosts on the IP addresses of the VLAN in the 10.1.50.0/24 subnet range. Computer A can communicate with computer B, but not with computer C or computer D. What is the most likely cause of this problem?
There is a native VLAN mismatch.
The link between Switch1 and Switch2 is up but not trunked.
The router is not properly configured for inter-VLAN routing.
VLAN 50 is not allowed to entering the trunk between Switch1 and Switch2.
There is a native VLAN mismatch.
The link between Switch1 and Switch2 is up but not trunked.
The router is not properly configured for inter-VLAN routing.
VLAN 50 is not allowed to entering the trunk between Switch1 and Switch2.
38. What happens to the member ports of a VLAN when the VLAN is deleted?
The ports cannot communicate with other ports.
The ports default back to the management VLAN.
The ports automatically become a part of VLAN1.
The ports remain a part of that VLAN until the switch is rebooted. They then become members of the management VLAN.
The ports cannot communicate with other ports.
The ports default back to the management VLAN.
The ports automatically become a part of VLAN1.
The ports remain a part of that VLAN until the switch is rebooted. They then become members of the management VLAN.
39. Refer to the exhibit. Computer B is unable to communicate with computer D. What is the most likely cause of this problem?
The link between the switches is up but not trunked.
VLAN 3 is not an allowed VLAN to enter the trunk between the switches.
The router is not properly configured to route traffic between the VLANs.
Computer D does not have a proper address for the VLAN 3 address space.
The link between the switches is up but not trunked.
VLAN 3 is not an allowed VLAN to enter the trunk between the switches.
The router is not properly configured to route traffic between the VLANs.
Computer D does not have a proper address for the VLAN 3 address space.
40. Refer to the exhibit. Company HR is adding PC4, a specialized application workstation, to a new company office. The company will add a switch, S3, connected via a trunk link to S2, another switch. For security reasons the new PC will reside in the HR VLAN, VLAN 10. The new office will use the 172.17.11.0/24 subnet. After installation, users on PC1 are unable to access shares on PC4. What is the likely cause?
The switch to switch connection must be configured as an access port to permit access to VLAN 10 on S3.
The new PC is on a different subnet so Fa0/2 on S3 must be configured as a trunk port.
PC4 must use the same subnet as PC1.
A single VLAN cannot span multiple switches.
The switch to switch connection must be configured as an access port to permit access to VLAN 10 on S3.
The new PC is on a different subnet so Fa0/2 on S3 must be configured as a trunk port.
PC4 must use the same subnet as PC1.
A single VLAN cannot span multiple switches.
41. What must the network administrator do to remove Fast Ethernet port fa0/1 from VLAN 2 and assign it to VLAN 3?
Enter the no vlan 2 and the vlan 3 commands in global configuration mode.
Enter the switchport access vlan 3 command in interface configuration mode.
Enter the switchport trunk native vlan 3 command in interface configuration mode.
Enter the no shutdown in interface configuration mode to return it to the default configuration and then configure the port for VLAN 3.
Enter the no vlan 2 and the vlan 3 commands in global configuration mode.
Enter the switchport access vlan 3 command in interface configuration mode.
Enter the switchport trunk native vlan 3 command in interface configuration mode.
Enter the no shutdown in interface configuration mode to return it to the default configuration and then configure the port for VLAN 3.