1. Which routing protocol is able to scale for large networks and utilizes non-backbone areas for expansion?
- EIGRP
- BGP
- OSPF*
- RIPv2
2. In the Cisco hierarchical design model, which layer is more likely to have a fixed configuration switch than the other layers?
- distribution
- transport
- internet
- access*
- core
3. A network engineer is interested in obtaining specific information relevant to the operation of both distribution and access layer Cisco devices. Which command provides common information relevant to both types of devices?
- show ip protocols
- show ip interface
- show cdp neighbors*
- show port-security
- show mac-address-table
4. A switched network has converged completely. All switches currently have a VTP revision number of 5. A new switch that has been configured as a VTP server is added to the network. The new switch has a VTP revision number of 4. What will occur within the network?
- The network will no longer share VLAN database updates.
- The newly added switch will automatically switch to VTP client mode.
- The VTP databases will remain unchanged in all switches with the exception of the newly added switch.*
- All switches in the network will update their VTP database to reflect the VTP database of the new switch.
5. A network administrator is adding a new VLAN for testing. The company uses VTP and the VLAN is not directly attached to either of the switches configured as VTP servers. What is the best method to add this VLAN to the network?
- Change the switch that has connected hosts in the new VLAN to be in VTP server mode.
- Configure a port on the VTP servers for the same VLAN as the new VLAN.
- Manually add the VLAN to the VLAN database of the VTP servers.*
- Configure interfaces on the switch that has connected hosts in the new VLAN and reboot the switch.
6. Which three pairs of trunking modes will establish a functional trunk link between two Cisco switches? (Choose three.)
- dynamic desirable – dynamic desirable*
- dynamic auto – dynamic auto
- dynamic desirable – dynamic auto*
- dynamic desirable – trunk*
- access – trunk
- access – dynamic auto
7. Refer to the exhibit. The configuration shows the commands entered by a network administrator for inter-VLAN routing. However, host PCA cannot communicate with PCB. Which part of the inter-VLAN configuration causes the problem?
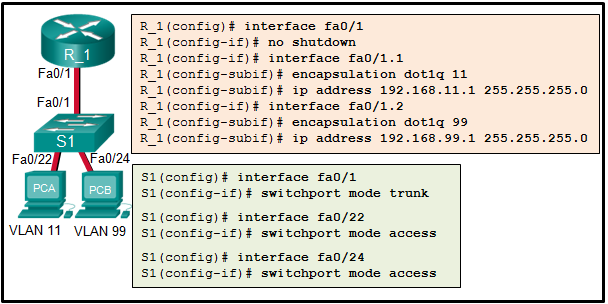

- trunking
- port mode on the two switch
- FastEthernet ports
- VLAN configuration*
- router port configuration
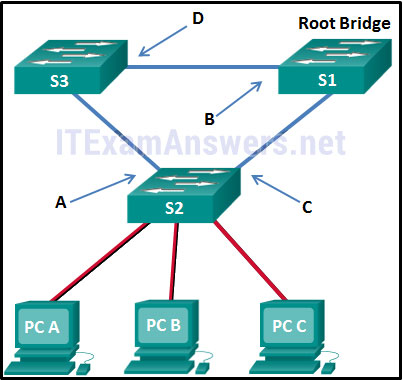
8. Refer to the exhibit. What is the role of the SW3 switch?
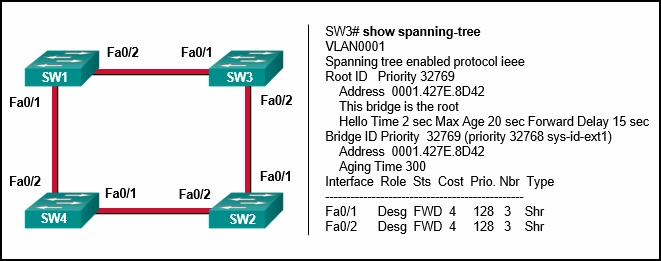

- designated switch
- edge switch
- root bridge*
- enabled bridge
- local bridge
9. Which spanning tree standard was developed by Cisco to provide separate instances of 802.1w per VLAN?
- RSTP
- 802.1D
- MSTP
- Rapid PVST+*
10. Which industry-wide specification was developed to decrease the time that is needed to move to the forwarding state by switch ports that are operating in a redundantly switched topology?
- VLSM
- PVST
- 802.1Q
- RSTP*
- VTP
11. Refer to the exhibit. A network administrator is verifying the bridge ID and the status of this switch in the STP election. Which statement is correct based on the command output?
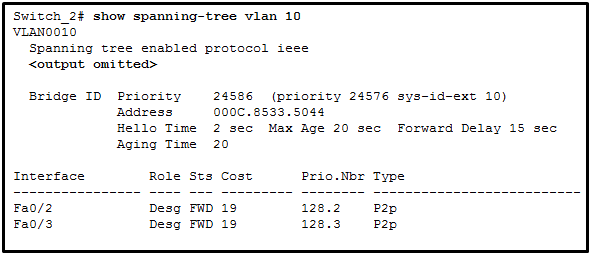

- The bridge priority of Switch_2 has been lowered to a predefined value to become the root bridge.*
- The bridge priority of Switch_2 has been lowered to a predefined value to become the backup root bridge.
- The STP instance on Switch_2 is failing due to no ports being blocked and all switches believing they are the root.
- The STP instance on Switch_2 is using the default STP priority and the election is based on Switch_2 MAC address.
12. Refer to the exhibit. Which switching technology would allow data to be transmitted over each access layer switch link and prevent the port from being blocked by spanning tree due to the redundant link?
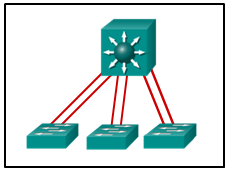

- EtherChannel*
- HSRP
- PortFast
- trunking
13. What are two advantages of EtherChannel? (Choose two.)
- Configuring the EtherChannel interface provides consistency in the configuration of the physical links.*
- Load balancing occurs between links configured as different EtherChannels.
- EtherChannel uses upgraded physical links to provide increased bandwidth.
- Spanning Tree Protocol views the physical links in an EtherChannel as one logical connection.*
- Spanning Tree Protocol ensures redundancy by transitioning failed interfaces in an EtherChannel to a forwarding state.
14. When EtherChannel is implemented, multiple physical interfaces are bundled into which type of logical connection?
- interface range
- loopback
- VLAN interface
- port channel*
15. When a range of ports is being configured for EtherChannel, which mode will configure LACP on a port only if the port receives LACP packets from another device?
- active
- auto
- desirable
- passive*
16. A new chief information officer (CIO) has requested implementation of a link-state dynamic routing protocol. Which two routing protocols fulfill this requirement? (Choose two.)
- RIPv2
- BGP
- OSPF*
- IS-IS*
- EIGRP
17. Refer to the exhibit. A network administrator is utilizing RIPv1 in the exhibited network topology. What would the router R2 do with a packet that is originating from the 192.168.4.0/24 network and destined for network 172.16.1.0/24?
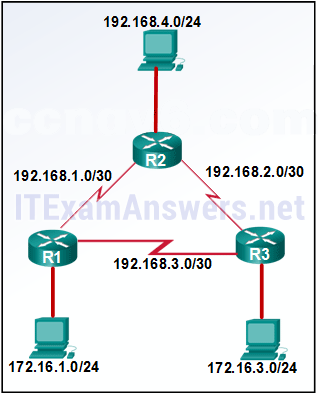

- The router will forward the packet to R1.
- The router will forward the packet to R3.
- The router will load balance and forward packets to both R1 and R3.*
- The router will drop the packet.
18. What best describes the operation of distance vector routing protocols?
- They use hop count as their only metric.
- They only send out updates when a new network is added.
- They send their routing tables to directly connected neighbors.*
- They flood the entire network with routing updates.
19. Which statement defines the speed of convergence of routing protocols?
- The time it takes a router to form a neighbor adjacency.
- The time it takes a router to learn about directly connected links.
- The time it takes a router to calculate the cost of a link.
- The time it takes a router within a network to forward routing information.*
20. What is associated with link-state routing protocols?
- low processor overhead
- poison reverse
- routing loops
- split horizon
- Shortest Path First calculations*
21. Which two pieces of information are contained within a link-state packet (LSP)? (Choose two.)
- hop count
- bandwidth*
- link type*
- delay
- load
22. What is a difference between the routing protocols EIGRP and OSPF?
- EIGRP uses hop count as the metric and OSPF uses cost as the metric.
- EIGRP is an implementation of EGP whereas OSPF is an implementation of IGP.
- EIGRP supports routing different network layer protocols whereas OSPF supports routing only IP-based protocols.*
- EIGRP only supports equal-cost load balancing whereas OSPF supports both equal-cost and unequal-cost load balancing.
23. What protocol is used by EIGRP for the delivery and receipt of EIGRP packets?
- RTP*
- TCP
- UDP
- ICMP
24. How is bandwidth to a destination network calculated by EIGRP?
- the lowest configured bandwidth of any interface along the route*
- the sum of the configured bandwidths of all interfaces along the path
- the highest configured bandwidth of any interface along the path
- the bandwidth of the ingress interface of the last hop router
25. Refer to the exhibit. A network administrator has attempted to implement a default route from R1 to the ISP and propagate the default route to EIGRP neighbors. Remote connectivity from the EIGRP neighbor routers to the ISP connected to R1 is failing. Based on the output from the exhibit, what is the most likely cause of the problem?
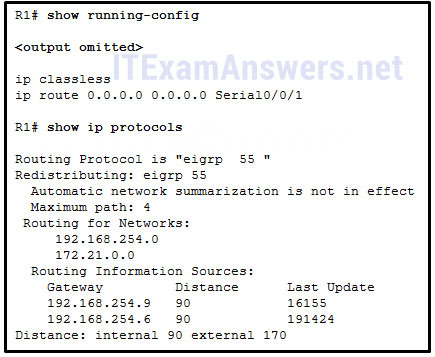

- The command default-information originate has not been issued on R1.
- There are no EIGRP neighbor relationships on R1.
- The ip route command must specify a next-hop IP address instead of an exit interface when creating a default route.
- The command redistribute static has not been issued on R1.*
- The network statement for the ISP connection has not been issued.
26. Refer to the exhibit. Which statement accurately reflects the configuration of routing on the HQ router?
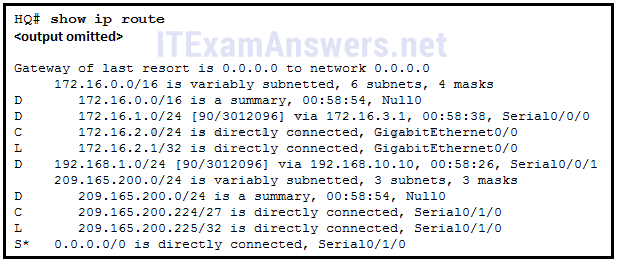

- A static default route was configured on this router.*
- A static default route was learned via EIGRP routing updates.
- The static default route should be redistributed using the default-information originate command.
- The IP address assigned to the GigabitEthernet0/0 interface is 172.16.2.0 255.255.255.0.
27. Which command would limit the amount of bandwidth that is used by EIGRP for protocol control traffic to approximately 128 Kb/s on a 1.544 Mb/s link?
- ip bandwidth-percent eigrp 100 8*
- maximum-paths 8
- variance 8
- traffic-share balanced
28. Which criterion is preferred by the router to choose a router ID?
- the IP address of the highest configured loopback interface on the router
- the IP address of the highest active interface on the router
- the router-id rid command*
- that is used for the area of a network that is affected when a device or network service experien
- the IP address of the highest active OSPF-enabled interface
29. What is the effect of entering the network 192.168.10.1 0.0.0.0 area 0 command in router configuration mode?
- The interface with the IPv4 address 192.168.10.1 will be a passive interface.
- OSPF advertisements will include the network on the interface with the IPv4 address 192.168.10.1.*
- This command will have no effect because it uses a quad zero wildcard mask.
- OSPF advertisements will include the specific IPv4 address 192.168.10.1.
30. Which three requirements are necessary for two OSPFv2 routers to form an adjacency? (Choose three.)
- The two routers must include the inter-router link network in an OSPFv2 network command.*
- The OSPFv2 process is enabled on the interface by entering the ospf process area-id command.
- The OSPF hello or dead timers on each router must match.*
- The OSPFv2 process ID must be the same on each router.
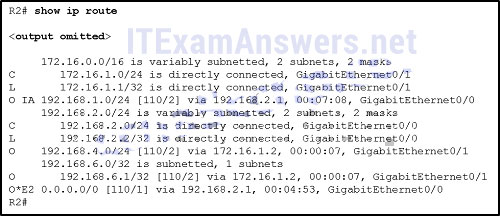
- The link interface subnet masks must match.*
- The link interface on each router must be configured with a link-local address.
31. Which type of OSPF router connects an OSPF area to non-OSPF routing domains?
- ABR
- ASBR*
- DR
- backbone router
32. Which function is performed by an OSPF ABR?
- flooding type 2 LSAs within an area
- originating type 5 LSAs into an area
- injecting type 3 LSAs into an area*
- advertising the router ID of any designated routers within an area
33. In which mode is the area area-id range address mask command issued when multiarea OSPF summarization is being configured?
- global configuration mode
- router configuration mode*
- interface configuration mode of area 0 interfaces
- interface configuration mode of all participating interfaces
34. Refer to the exhibit. What are three resulting DR and DBR elections for the given topology? (Choose three.)
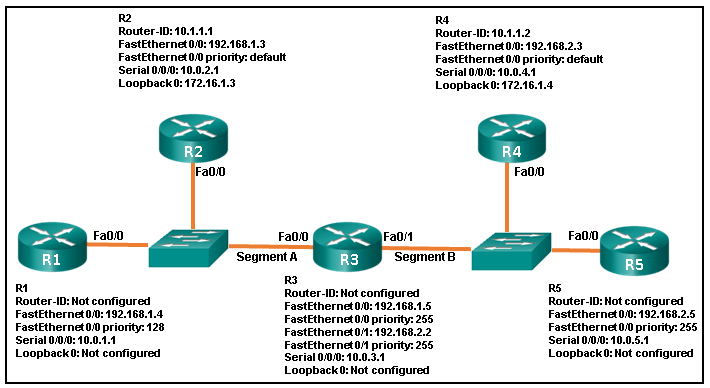

- R4 is BDR for segment B.
- R4 is DR for segment B.
- R3 is DR for segment A.*
- R2 is DR for segment A.
- R3 is BDR for segment B.*
- R5 is DR for segment B.*
35. Refer to the exhibit. How did this router learn of the highlighted route in the routing table?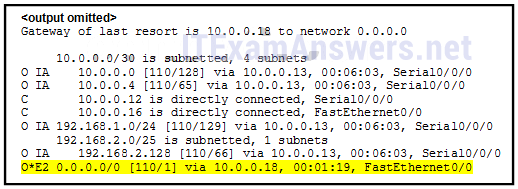

- by entering the router configuration mode command default-information originate
- by entering the global configuration mode command ip route 0.0.0.0 0.0.0.0 interface-type interface-number
- by entering the global configuration mode command ip route 0.0.0.0 0.0.0.0 ip-address
- by receiving an update from another OSPF router that is running another routing protocol
- by receiving an update from another OSPF router that has the default-information originate command configured*
36. Which command can be used to view OSPF adjacencies with neighboring routers along with the transition state?
- show ip protocols
- show ip ospf neighbor*
- show ip ospf interface
- show running-config
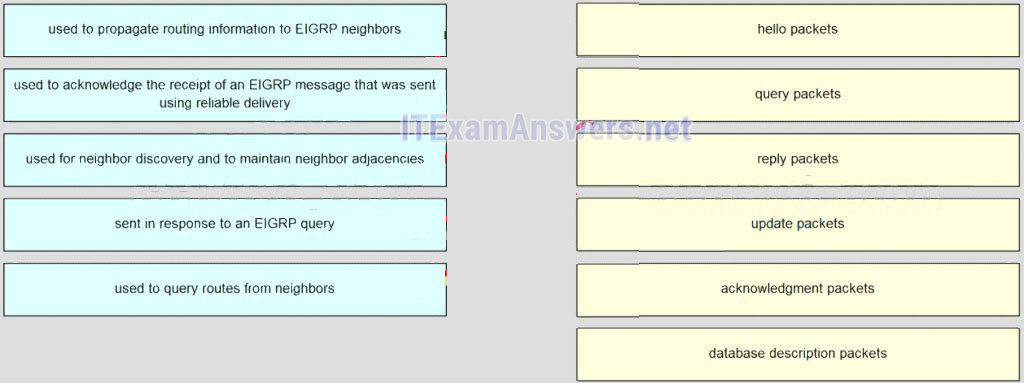
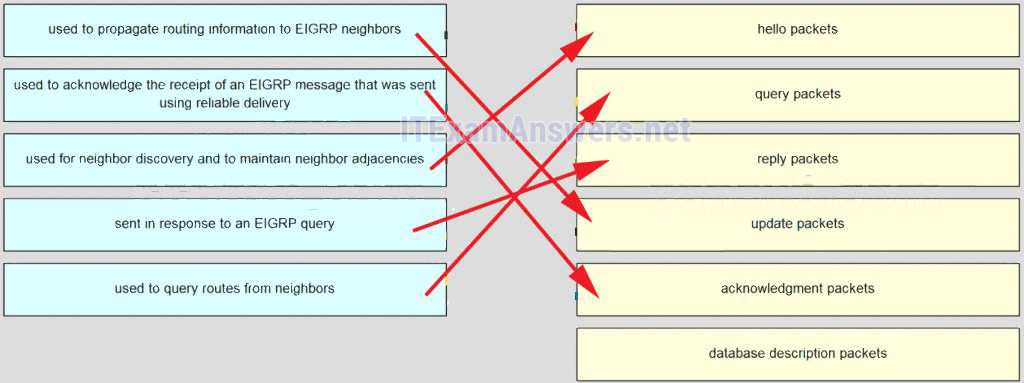
37. Match the description to the EIGRP packet type. (Not all options are used.)


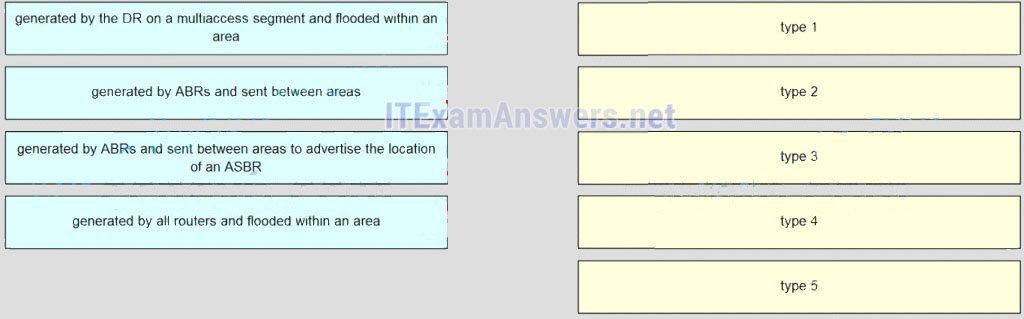
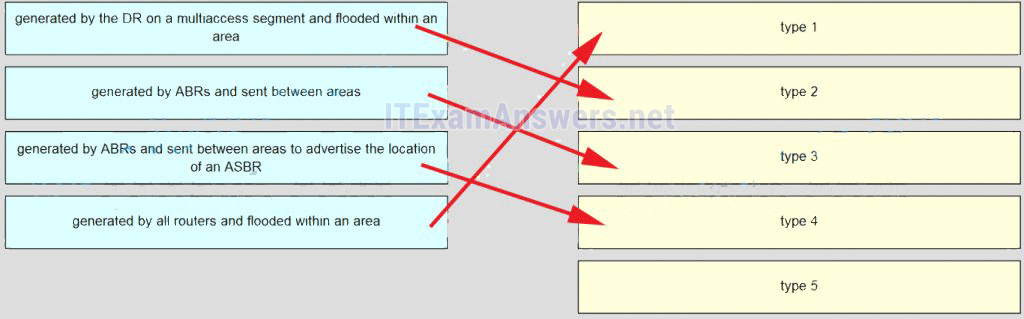
37. Match each description to its corresponding LSA type. (Not all options are used.)


39. What is the term that is used for the area of a network that is affected when a device or network service experiences problems?
- failure domain*
- collision domain
- broadcast domain
- user domain
40. What term is used to express the thickness or height of a switch?
- rack unit*
- port density
- domain size
- module size
41. Which configuration changes will increment the configuration revision number on the VTP server?
- configuring trunk links on the VTP server
- configuring or changing the VTP password
- configuring or changing the VTP domain name
- configuring or changing the VTP version number
- configuring or deleting a VLAN or creating a VLAN name*
42. What are three characteristics of VTP? (Choose three.)
- In the default VTP mode, VLANs can be created and modified on a switch.*
- Switches in VTP server mode store VLANs in the vlan.dat database.*
- VTP-enabled switches exchange three types of advertisements: summary routes, subnet advertisements, and advertisement requests from transparent bridges.
- The switch configuration must be saved and the switch reloaded to reset a configuration revision number.
- VTP updates are exchanged across trunk links only.*
- Switches in different VTP domains can exchange updates if revision numbers are the same.
43. What is the purpose of the vlan.dat file on a switch?
- It holds the running configuration.
- It holds the saved configuration.
- It holds the VLAN database.*
- It holds the operating system.
44. What eliminates switching loops?
- hold-down timer
- spoison reverse
- Spanning Tree Protocol*
- Time to Live
- VTP
45. A small company network has six interconnected Layer 2 switches. Currently all switches are using the default bridge priority value. Which value can be used to configure the bridge priority of one of the switches to ensure that it becomes the root bridge in this design?
- 1
- 28672*
- 32768
- 34816
- 61440
46. What is the value used to determine which port on a non-root bridge will become a root port in a STP network?
- the highest MAC address of all the ports in the switch
- the lowest MAC address of all the ports in the switch
- the VTP revision number
- the path cost*
47. Which three STP states were replaced with the RSTP discarding state? (Choose three.)
- listening*
- learning
- blocking*
- disabled*
- forwarding
48. As the network administrator you have been asked to implement EtherChannel on the corporate network. What does this configuration consist of?
- providing redundant links that dynamically block or forward traffic
- grouping multiple physical ports to increase bandwidth between two switches*
- grouping two devices to share a virtual IP address
- providing redundant devices to allow traffic to flow in the event of device failure
49. Which command will start the process to bundle two physical interfaces to create an EtherChannel group via LACP?
- channel-group 2 mode auto
- interface port-channel 2
- channel-group 1 mode desirable
- interface range GigabitEthernet 0/4 – 5*
50. A network administrator is analyzing the features that are supported by different first-hop router redundancy protocols. Which statement is a feature that is associated with GLBP?
- GLBP allows load balancing between routers.*
- It is nonproprietary.
- It uses a virtual router master.
- It works together with VRRP.
51. A network administrator configured an EtherChannel link with three interfaces between two switches. What is the result if one of the three interfaces is down?
- The EtherChannel fails.
- The remaining two interfaces continue to load balance traffic.*
- The remaining two interfaces become separate links between the two switches.
- One interface becomes an active link for data traffic and the other becomes a backup link.
52. When EtherChannel is configured, which mode will force an interface into a port channel without exchanging aggregation protocol packets?
- active
- auto
- on*
- desirable
53. Refer to the exhibit. A network administrator is reviewing the configuration of switch S1. Which protocol has been implemented to group multiple physical ports into one logical link?
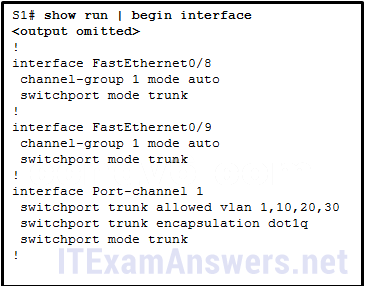

- PAgP*
- DTP
- LACP
- STP
54. What is the term used to describe a network topology where the subnets from a major classful network address space are separated from each other by addresses from a different major classful network address?
- multihomed network
- converged network
- discontiguous network*
- data network
55. What type of packets are sent when there is a change in the EIGRP topology?
- hello
- triggered bounded update*
- acknowledge
- reply
56. Which three pieces of information does a link-state routing protocol use initially as link-state information for locally connected links? (Choose three.)
- the link router interface IP address and subnet mask*
- the type of network link*
- the link next-hop IP address
- the link bandwidth
- the cost of that link*
57. What indicates to a link-state router that a neighbor is unreachable?
- if the router no longer receives routing updates
- if the router no longer receives hello packets*
- if the router receives an update with a hop count of 16
- if the router receives an LSP with previously learned information
58. What are three features of EIGRP? (Choose three.)
- uses the Shortest Path First algorithm
- establishes neighbor adjacencies*
- uses the Reliable Transport Protocol*
- sends full routing table updates periodically
- broadcasts updates to all EIGRP routers
- supports equal and unequal cost load balancing*
59. What capability do protocol-dependent modules provide to the EIGRP routing protocol?
- route different Layer 3 protocols*
- exchange summary routes between areas
- combine routes learned from different protocols into a single routing table
- load balance between routing protocols
60. Which command should be used to configure EIGRP to only advertise the network that is attached to the gigabit Ethernet 0/1 interface?
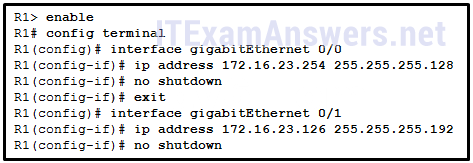

- network 172.16.23.64 0.0.0.63*
- network 172.16.23.0 255.255.255.192
- network 172.16.23.64 0.0.0.127
- network 172.16.23.0 255.255.255.128
61. Which command will configure an IPv6 default static route?
- router(config)# ipv6 ::/64 s0/0/0
- router(config-rtr)# redistribute static
- router(config)# ipv6 route ::/0 s0/0/0*
- router(config)# ipv6 unicast-routing
62. What routing protocol can be configured to load balance across paths with unequal metrics through the use of the variance command?
- EIGRP*
- OSPF
- OSPFv3
- RIPng
63. What are two features of a link-state routing protocol? (Choose two.)
- Routers send periodic updates only to neighboring routers.
- Routers send triggered updates in response to a change.*
- Routers create a topology of the network by using information from other routers.*
- The database information for each router is obtained from the same source.
- Paths are chosen based on the lowest number of hops to the designated router.
64. A router is participating in an OSPFv2 domain. What will always happen if the dead interval expires before the router receives a hello packet from an adjacent DROTHER OSPF router?
- OSPF will run a new DR/BDR election.
- SPF will run and determine which neighbor router is “down”.
- A new dead interval timer of 4 times the hello interval will start.
- OSPF will remove that neighbor from the router link-state database.*
65. In an OSPFv2 configuration, what is the effect of entering the command network 192.168.1.1 0.0.0.0 area 0?
- It changes the router ID of the router to 192.168.1.1.
- It enables OSPF on all interfaces on the router.
- It tells the router which interface to turn on for the OSPF routing process.*
- It allows all 192.168.1.0 networks to be advertised.
66. What does the cost of an OSPF link indicate?
- A higher cost for an OSPF link indicates a faster path to the destination.
- Link cost indicates a proportion of the accumulated value of the route to the destination.
- Cost equals bandwidth.
- A lower cost indicates a better path to the destination than a higher cost does.*
67. Which two addresses represent valid destination addresses for an OSPFv3 message? (Choose two.)
- FF02::5*
- 224.0.0.5FF02::A
- FE80::42*
- 2001:db8:acad:1::1
68. What information is contained in OSPF type 3 LSAs?
- networks reachable in other areas*
- networks learned from other routing protocols
- the router ID of the DR to all routers in the area
- the router ID of an ASBR and the route to reach it
69. Refer to the exhibit. For the given topology, what are three results of the OSPF DR and BDR elections? (Choose three.)
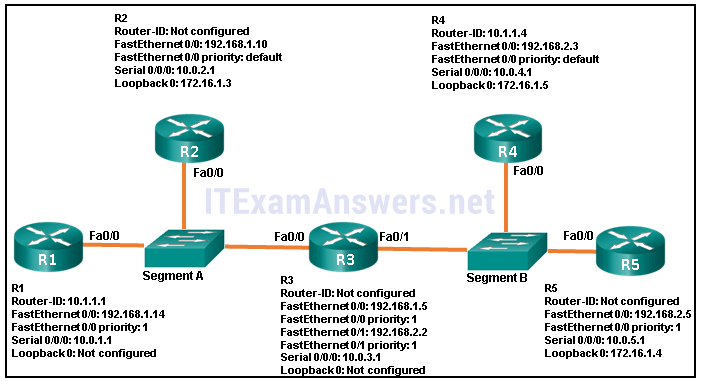

- R1 is BDR for segment A.
- R2 is DR for segment A.
- R3 is DR for segment A.*
- R4 is DR for segment B.
- R5 is BDR for segment B.*
- R3 is DR for segment B.*
70. Refer to the exhibit. In this scenario, Area 40 cannot be connected directly to Area 0. Which OSPF network type must be configured in Area 1 to connect these areas?
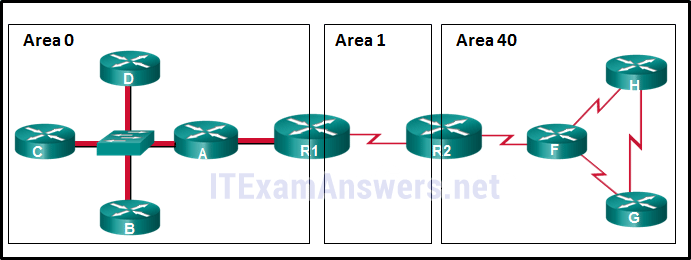

- point-to-point
- virtual link*
- point-to-multipoint
- nonbroadcast multiaccess
71. Refer to the exhibit. What method can be used to enable an OSPF router to advertise a default route to neighboring OSPF routers?
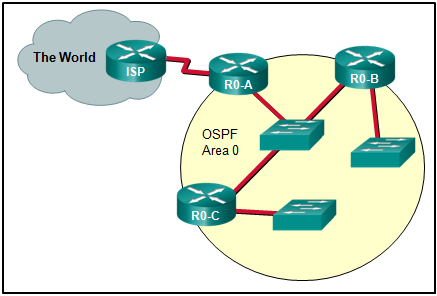

- Use a static route pointing to the ISP and redistribute it.
- Use a static route pointing to the ISP and redistribute it.
- Use the redistribute static command on R0-A.
- Use the default-information originate command on ISP.
- Use the default-information originate command on R0-A.*
72. Refer to the exhibit. A network administrator has configured the OSPF timers to the values that are shown in the graphic. What is the result of having those manually configured timers?
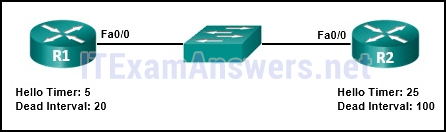

- The R1 dead timer expires between hello packets from R2.*
- R1 automatically adjusts its own timers to match the R2 timers.
- The hello timer on R2 expires every ten seconds.
- The neighbor adjacency has formed.
73. Refer to the exhibit.A network administrator has configured OSPFv2 on the two Cisco routers as shown. The routers are unable to form a neighbor adjacency. What should be done to fix the problem?
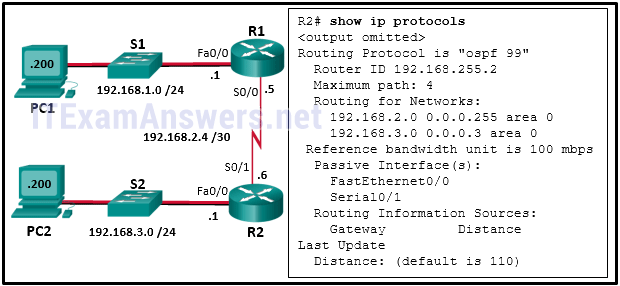

- Implement the command no passive-interface Serial0/1.
- Implement the command network 192.168.2.4 0.0.0.3 area 0 on router R2.
- Implement the command network 192.168.3.0 0.0.0.255 area 0 on router R2.
- Change the router-id of router R2 to 2.2.2.2.
74. A network administrator has configured an EtherChannel between two switches that are connected via four trunk links. If the physical interface for one of the trunk links changes to a down state, what happens to the EtherChannel?
- Spanning Tree Protocol will transition the failed physical interface into forwarding mode.
- Spanning Tree Protocol will recalculate the remaining trunk links.
- The EtherChannel will transition to a down state.
- The EtherChannel will remain functional.*
75. Which mode configuration setting would allow formation of an EtherChannel link between switches SW1 and SW2 without sending negotiation traffic?
- SW1: on
SW2: on* - SW1: desirable
SW2: desirable - SW1: auto
SW2: auto
PortFast enabled on both switches - SW1: auto
SW2: auto
trunking enabled on both switches - SW1: passive
SW2: active
76. Which two statements are correct about EIGRP acknowledgment packets? (Choose two.)
- The packets are used to discover neighbors that are connected on an interface.
- The packets are sent as unicast.*
- The packets require confirmation.
- The packets are unreliable.*
- The packets are sent in response to hello packets.
77. A set of switches is being connected in a LAN topology. Which STP bridge priority value will make it least likely for the switch to be selected as the root?
- 61440*
- 4096
- 65535
- 32768
78. A network administrator is analyzing the features that are supported by different first-hop router redundancy protocols. Which statement describes a feature that is associated with HSRP?
- HSRP uses active and standby routers.*
- It uses ICMP messages in order to assign the default gateway to hosts.
- It allows load balancing between a group of redundant routers.
- HSRP is nonproprietary.
79. The graphic shows the following information: Switch S1 (the root bridge) uses a port that is labeled B to connect to switch S3 on a port labeled D. S3 is connected to switch S2 on a port labeled A. S2 uses a port labeled C to connect to S1. S2 is connected also to three PC workstations labeled A, B, and C. Refer to the exhibit. What are the possible port roles for ports A, B, C, and D in this RSTP-enabled network?

- alternate, root, designated, root
- designated, alternate, root, root
- alternate, designated, root, root*
- designated, root, alternate, root
80. Refer to the exhibit. What are two results of issuing the displayed commands on S1, S2, and S3? (Choose two.)


- S2 can become root bridge if S1 fails.*
- S2 can become root bridge if S3 fails.
- S1 will automatically adjust the priority to be the lowest*.
- S3 can be elected as a secondary bridge.
- S1 will automatically adjust the priority to be the highest.
81. Which statement describes a characteristic of OSPF external routes?
- The cost of a type 1 route is always the external cost, regardless of the interior cost to reach that route.
- The difference between type 1 and type 2 is in the way the cost of the route is being calculated.*
- A type 2 route is always preferred over a type 1 route for the same destination.
- Type 1 and type 2 external routes in IPv4 networks are represented in the routing table by EX1 and EX2, respectively.
82. By default, how many equal cost routes to the same destination can be installed in the routing table of a Cisco router?
- 2
- 4*
- 16
- 32
83. An EIGRP router loses the route to a network. Its topology table contains two feasible successors to the same network. What action will the router take?
- The best alternative backup route is immediately inserted into the routing table.*
- The router will query neighbors for an alternate route.
- The DUAL algorithm is recomputed to find an alternate route.
- The router uses the default route.
84. A network administrator is analyzing first-hop router redundancy protocols. What is a characteristic of VRRPv3?
- It allows load balancing between routers.
- VRRPv3 is Cisco proprietary.
- It supports IPv6 and IPv4 addressing.*
- It works together with HSRP.
85. What is the function of STP in a scalable network?
- It combines multiple switch trunk links to act as one logical link for increased bandwidth.
- It protects the edge of the enterprise network from malicious activity.
- It disables redundant paths to eliminate Layer 2 loops.*
- It decreases the size of the failure domain to contain the impact of failures.
86. When should EIGRP automatic summarization be turned off?
- when a router has less than five active interfaceswhen a router has more than three active interfaces
- when a network contains discontiguous network addresses*
- when a router has not discovered a neighbor within three minutes
- when a network addressing scheme uses VLSM
87. Which characteristic would most influence a network design engineer to select a multilayer switch over a Layer 2 switch?
- ability to aggregate multiple ports for maximum data throughput
- ability to have multiple forwarding paths through the switched network based on VLAN number(s)
- ability to provide power to directly-attached devices and the switch itself
- ability to build a routing table*
88. What are two features of OSPF interarea route summarization? (Choose two.)
- Route summarization results in high network traffic and router overhead.
- Routes within an area are summarized by the ABR.*
- Type 3 and type 5 LSAs are used to propagate summarized routes by default.
- ASBRs perform all OSPF summarization.
- ABRs advertise the summarized routes into the backbone.*
89. Refer to the exhibit. Which two conclusions can be derived from the output? (Choose two.)
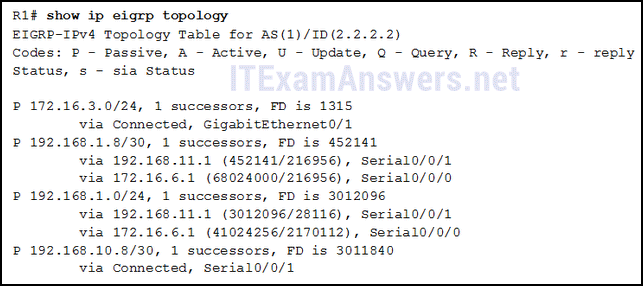

- There is one feasible successor to network 192.168.1.8/30.*
- The network 192.168.10.8/30 can be reached through 192.168.11.1.
- The reported distance to network 192.168.1.0/24 is 41024256.
- The neighbor 172.16.6.1 meets the feasibility condition to reach the 192.168.1.0/24 network.*
- Router R1 has two successors to the 172.16.3.0/24 network.
90. What are the only two roles that permit an OSPF router to be configured for summarization? (Choose two.)
- designated router
- backbone router
- internal router
- autonomous system boundary router*
- area border router*
91. A network engineer examining the operation of EIGRP on a router notices that one particular route is in an active state. What can the engineer determine about this route?
- Data packets to be sent to the specified network will be forwarded on this route.
- The Diffusing Update Algorithm has determined a successor and a feasible successor for this route.
- The EIGRP processes are still calculating the administrative distance for this route.
- EIGRP query messages are being sent to other routers requesting paths to this network.*
92. A router needs to be configured to route within OSPF Area 0. Which two commands are required to accomplish this? (Choose two.)
- RouterA(config)# router ospf 0
- RouterA(config-router)# network 192.168.2.0 255.255.255.0 0
- RouterA(config-router)# network 192.168.2.0 0.0.0.255 area 0*
- RouterA(config-router)# network 192.168.2.0 0.0.0.255 0
- RouterA(config)# router ospf 1*
93. Refer to the exhibit. What are three resulting DR and BDR elections for the given topology? (Choose three.)
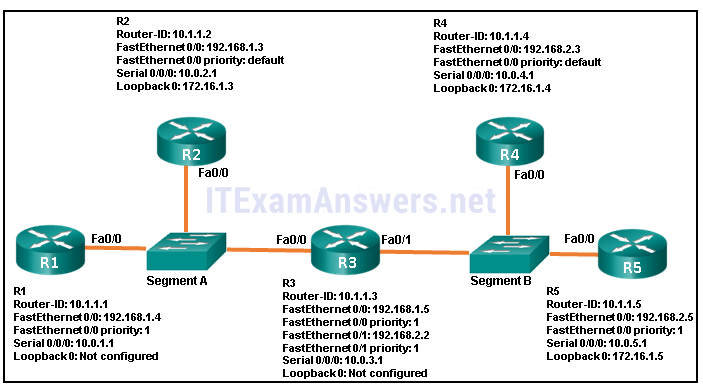

- R4 is BDR for segment B.*
- R1 is DR for segment A.
- R5 is DR for segment B.*
- R3 is DR for segment B.
- R3 is DBR for segment B.
- R2 is BDR for segment A.*
94. Which statement is true about the states of the IEEE 802.1D Spanning Tree Protocol?
- Ports must be blocked before they can be placed in the disabled state.
- Ports listen and learn before going into the forwarding state.*
- Ports are manually configured to be in the forwarding state.
- It takes 15 seconds for a port to go from blocking to forwarding.
95. What is one reason to use the ip ospf priority command when the OSPF routing protocol is in use?
- to influence the DR/BDR election process*
- to streamline and speed up the convergence process
- to provide a backdoor for connectivity during the convergence process
- to activate the OSPF neighboring process
96. A network administrator is configuring EIGRP load balancing with the commands:
Router(config)# router eigrp 1
Router(config-router)# variance 3
Router(config-router)# end
What is a direct result of entering these commands?
Router(config)# router eigrp 1
Router(config-router)# variance 3
Router(config-router)# end
What is a direct result of entering these commands?
- Any feasible successor routes to the same destination network with a metric, equal to or less than 3 times that of the successor, will be installed in the routing table.*
- Up to three equal cost routes to the same destination can be installed in the routing table.
- No matter whether the metric is equal or unequal, up to three routes to the same destination can be installed in the routing table.
- Up to three unequal cost routes to the same destination can be installed in the routing table.
97. What are two load-balancing methods in the EtherChannel technology? (Choose two.)
- source IP to destination IP*
- source MAC to destination MAC*
- combination of source MAC and IP to destination MAC and IP
- combination of source port and IP to destination port and IP
- source port to destination port
98. Which statement describes the autonomous system number used in EIGRP configuration on a Cisco router?
- It carries the geographical information of the organization.
- It identifies the ISP that provides the connection to network of the organization.
- It functions as a process ID in the operation of the router.*
- It is a globally unique autonomous system number that is assigned by IANA.
99. An administrator was troubleshooting a router-on-a-stick topology and concluded that the problem was related to the configuration of VLANs on the router subinterfaces. Which two commands can the administrator use in the router to identify the problem? (Choose two.)
- show controllersshow vlan
- show running-config*
- show ip interface*
- show ip protocols
100. What is a key distinction between classful and classless routing protocols?
- Classful routing protocols do not send subnet mask information in their routing updates.*
- Classful routing protocols are better suited for implementation in discontiguous networks.
- Classless routing protocols are not scalable.
- Classless routing protocols do not allow for route summarization.
101. Refer to the exhibit. The network administrator configures both switches as displayed. However, host C is unable to ping host D and host E is unable to ping host F. What action should the administrator take to enable this communication?
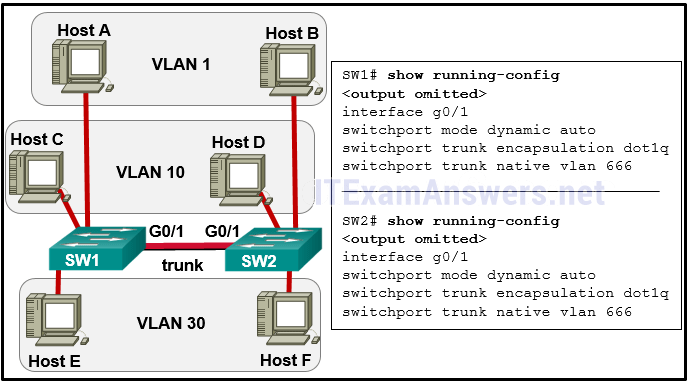

- Associate hosts A and B with VLAN 10 instead of VLAN 1.
- Configure either trunk port in the dynamic desirable mode.*
- Include a router in the topology.
- Remove the native VLAN from the trunk.
- Add the switchport nonegotiate command to the configuration of SW2.
102. Which is a characteristic of EtherChannel?
- STP will not block redundant EtherChannel bundles between two switches.
- STP treats all interfaces in a bundle as a single logical link.*
- EtherChannel configuration is applied to each physical port.
- EtherChannel uses physical ports that have been upgraded to provide a faster connection.
103. The topology displays seven routers with four alternative ways to get from source to destination:
Path cost for R1-R3-R4-R5-R6-R7 = 29
Path cost for R1-R3-R2-R6-R7 = 42
Path cost for R1-R2-R6-R7 = 43
Path cost for R1-R4-R5-R6-R7 = 31
The source is the LAN that is connected to R1. The destination is the LAN that is connected to R7.
Refer to the exhibit. A network administrator has configured OFPF in the topology as shown. What is the preferred path to get from the LAN network that is connected to R1 to the LAN network that is connected to R7?
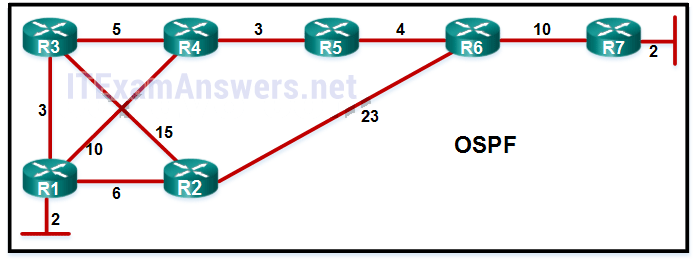
Path cost for R1-R3-R4-R5-R6-R7 = 29
Path cost for R1-R3-R2-R6-R7 = 42
Path cost for R1-R2-R6-R7 = 43
Path cost for R1-R4-R5-R6-R7 = 31
The source is the LAN that is connected to R1. The destination is the LAN that is connected to R7.
Refer to the exhibit. A network administrator has configured OFPF in the topology as shown. What is the preferred path to get from the LAN network that is connected to R1 to the LAN network that is connected to R7?

- R1-R2-R6-R7
- R1-R3-R2-R6-R7
- R1-R3-R4-R5-R6-R7*
- R1-R4-R5-R6-R7
104. Four switches, labeled as SW1, SW2, SW3, and SW4, are interconnected. SW1 interface Gi 1/1 is connected to SW4 interface Gi 1/2. SW1 interface Gi 1/2 is connected to SW3 interface Gi 1/1. SW2 interface Gi 1/1 is connected to SW3 interface Gi 1/2. SW2 interface Gi 1/2 is connected to SW4 interface Gi 1/1. There are four text boxes. Text box 1 shows the following:
SW1 Priority 32769
MAC Address = 00E0.000B.2222Text box 2 shows the following:
SW2 Priority 32769
MAC Address = 00E0.000C.3333Text box 3 shows the following:
SW3 Priority 32769
MAC Address = 00E0.000A.1111Text box 4 shows the following:
SW4 Priority 32769
MAC Address = 00E0.000D.4444
MAC Address = 00E0.000B.2222Text box 2 shows the following:
SW2 Priority 32769
MAC Address = 00E0.000C.3333Text box 3 shows the following:
SW3 Priority 32769
MAC Address = 00E0.000A.1111Text box 4 shows the following:
SW4 Priority 32769
MAC Address = 00E0.000D.4444
Refer to the exhibit. Which switch will be elected the root bridge and which switch will place a port in blocking mode? (Choose two.)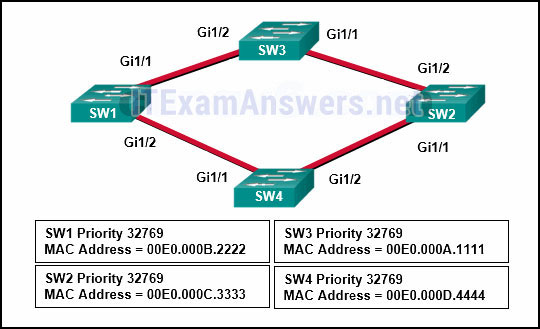

- SW1 will become the root bridge.
- SW4 will become the root bridge.
- SW2 will become the root bridge.
- SW2 will get a port blocked.
- SW3 will become the root bridge.*
- SW4 will get a port blocked.*
105. Which command can be used by an administrator to display a list of interfaces that are enabled for OSPFv3?
- show ipv6 protocols*
- show ipv6 neighbor
- show ipv6 route ospf
- show ipv6 ospf
106. What EIGRP packet type is used by EIGRP routers to discover neighbors on directly connected links?
- acknowledgment
- query
- Hello*
- update
107. Refer to the exhibit. All the displayed switches are Cisco 2960 switches with the same default priority and operating at the same bandwidth. Which three ports will be STP designated ports? (Choose three.)
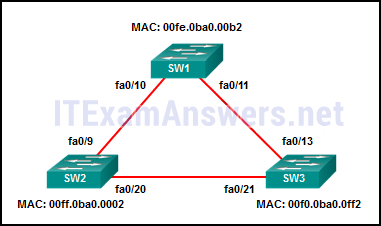

- fa0/9fa0/20
- fa0/13*
- fa0/21*
- fa0/10*
- fa0/11
108. How is the router ID for an OSPFv3 router determined?
- the highest IPv6 address on an active interface
- the highest EUI-64 ID on an active interface
- the highest IPv4 address on an active interface*
- the lowest MAC address on an active interface
109. Which step can be taken to ensure that a switch added to the network does not overwrite the VLAN databases on existing switches in the same VTP domain?
- Erase the startup configuration and reboot the switch.
- Reset the switch VTP revision number to 0.*
- Delete any configured VLANs and reboot the switch.
- Change the VTP mode to client.
110. A network administrator is planning to add a new switch to the network. What should the network administrator do to ensure the new switch exchanges VTP information with the other switches in the VTP domain?
- Configure the correct VTP domain name and password on the new switch.*
- Associate all ports of the new switch to a VLAN that is not VLAN 1.
- Configure all ports on the new switch to access mode.
- Configure the VLANs on the new switch.
111. Refer to the exhibit. A network administrator has configured OSPFv2 on the two Cisco routers as shown. PC1 is unable to communicate with PC2. What should be done to fix the problem?
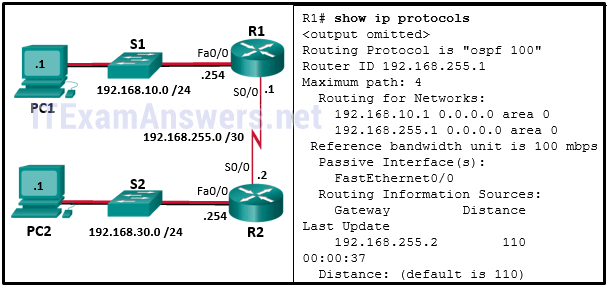

- Add the network 192.168.255.0 0.0.0.3 area 0 command to router R1 and remove the network 192.168.255.1 0.0.0.0 area 0 command.
- Add the network 192.168.255.2 0.0.0.0 area 0 command to router R1 and remove the network 192.168.255.1 0.0.0.0 area 0 command.
- Add the network 192.168.10.0 0.0.0.255 area 0 command to router R1 and remove the network 192.168.10.1 0.0.0.0 area 0 command.*
- Add the passive-interface S0/0 command to router R1.
112. When the show spanning-tree vlan 33 command is issued on a switch, three ports are shown in the forwarding state. In which two port roles could these interfaces function while in the forwarding state? (Choose two.)
- blocked
- alternate
- disabled
- Designated*
- Root*
113. Which two parameters must match on the ports of two switches to create a PAgP EtherChannel between the switches? (Choose two.)
- MAC address
- VLAN information*
- port ID
- Speed*
- PAgP mode
114. What is the final operational state that will form between an OSPF DR and a DROTHER once the routers reach convergence?
- established
- loading
- two-way
- Full*
115. Which command is used to display the bandwidth of an interface on an EIGRP-enabled router?
- show ip interface brief
- show ip protocols
- show interfaces*
- show ip route
116. How are externally learned EIGRP routes identified in the routing table?
- EX*
- *
- O1 E
- D
117. What does the SPF algorithm consider to be the best path to a network?
- The path that includes the fastest single bandwidth link.
- The path with the smallest delays.
- The path that includes the fastest cumulative bandwidth links.*
- The path with the least number of hops.
118. Which protocol does EIGRP use for the transportation of EIGRP packets?
- Transmission Control Protocol
- User Datagram Protocol
- Real-Time Transport Protocol
- Reliable Transport Protocol*
119. What is a function of OSPF hello packets?
- to ensure database synchronization between routers
- to discover neighbors and build adjacencies between them*
- to send specifically requested link-state records
- to request specific link-state records from neighbor routers
120. Refer to the exhibit. The configuration shows commands entered by a network administrator for inter-VLAN routing. However, host H1 cannot communicate with H2. Which part of the inter-VLAN configuration causes the problem?
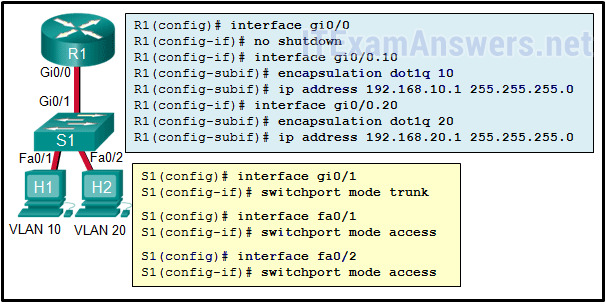

- trunking
- port mode on the two switch FastEthernet ports
- VLAN configuration*
- router port configuration
121. A network designer is considering whether to implement a switch block on the company network. What is the primary advantage of deploying a switch block?
- A single core router provides all the routing between VLANs.
- The failure of a switch block will not impact all end users.*
- This is a security feature that is available on all new Catalyst switches.
- This is network application software that prevents the failure of a single network device.
122. Which address is used by an IPv6 EIGRP router as the source for hello messages?
- the 32-bit router ID
- the IPv6 global unicast address that is configured on the interface
- the all-EIGRP-routers multicast address
- the interface IPv6 link-local address*
123. Which routing table descriptor is used to identify the OSPF networks advertised by type 1 LSAs?
- O*
- O IA
- O E2
- O E1
124. What does an OSPF area contain?
- routers whose SPF trees are identical
- routers that share the same process ID
- routers that have the same link-state information in their LSDBs*
- routers that share the same router ID
125. What two values must match between two EIGRP directly connected neighbors to establish and maintain an adjacency? (Choose two.)
- autonomous system number*
- metric parameters*
- hello timers
- router ID
- Area ID
126. When will a router that is running EIGRP put a destination network in the active state?
- when the EIGRP domain is converged
- when there is outgoing traffic toward the destination network
- when there is an EIGRP message from the successor of the destination network
- when the connection to the successor of the destination network fails and there is no feasible successor available*
127. Refer to the exhibit. Switch SW-A is to be used as a temporary replacement for another switch in the VTP Student domain. What two pieces of information are indicated from the exhibited output? (Choose two.)
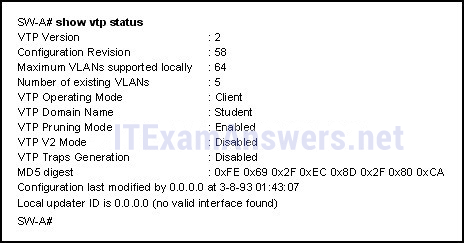

- The other switches in the domain can be running either VTP version 1 or 2.
- VLAN configuration changes made on this switch will be sent to other devices in the VTP domain.
- VTP will block frame forwarding on at least one redundant trunk port that is configured on this switch.
- This switch will update its VLAN configuration when VLAN changes are made on a VTP server in the same domain.*
- There is a risk that the switch may cause incorrect VLAN information to be sent through the domain.*
128. Refer to the exhibit. Which route or routes will be advertised to the router ISP if autosummarization is enabled?
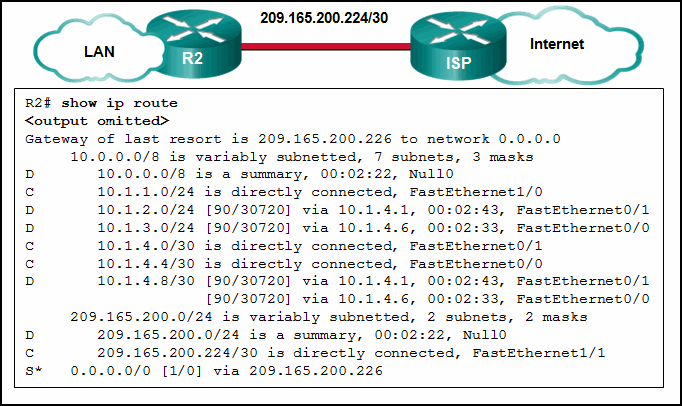
- 10.0.0.0/8*
- 10.1.0.0/16
- 10.1.0.0/28
- 10.1.1.0/24
- 10.1.2.0/24
- 10.1.3.0/24
- 10.1.4.0/28
129. What are two reasons to install a single 48-port fixed configuration switch, rather than two 24-port fixed configuration switches, in a wiring closet that supports two classrooms? (Choose two.)
- more ports available for end devices*
- more power provided to each port
- higher uplink speeds
- reduced power and space requirements*
- reduced number of VLANs/broadcast domains
130. What is a characteristic of spanning tree?
- It prevents propagation of Layer 2 broadcast frames.
- It is enabled by default on Cisco switches.*
- It is used to discover information about an adjacent Cisco device.
- It has a TTL mechanism that works at Layer 2.
131. A network administrator enters the spanning-tree portfast bpduguard default command. What is the result of this command being issued on a Cisco switch?
- Any switch port will be error-disabled if it receives a BPDU.
- Any trunk ports will be allowed to connect to the network immediately, rather than waiting to converge.
- Any switch port that has been configured with PortFast will be error-disabled if it receives a BPDU.*
- Any switch port that receives a BPDU will ignore the BPDU message.
132. Refer to the exhibit. A network administrator would like to implement dynamic routing within a small network environment as shown in the exhibit. Which routing protocol would be a viable solution?
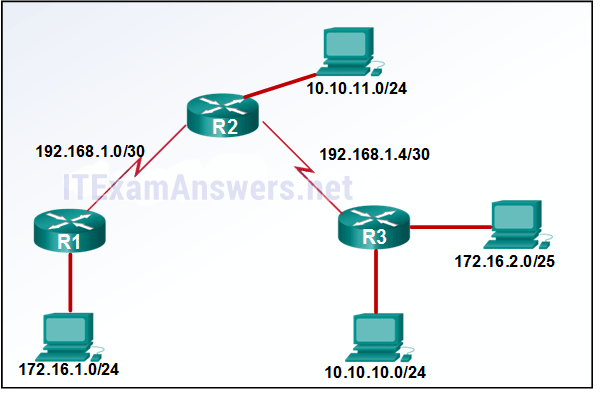

- BGP
- IGRP
- RIPv1
- EIGRP*
133. Refer to the exhibit. R1 and R2 are OSPFv3 neighbors. Which address would R1 use as the next hop for packets that are destined for the Internet?
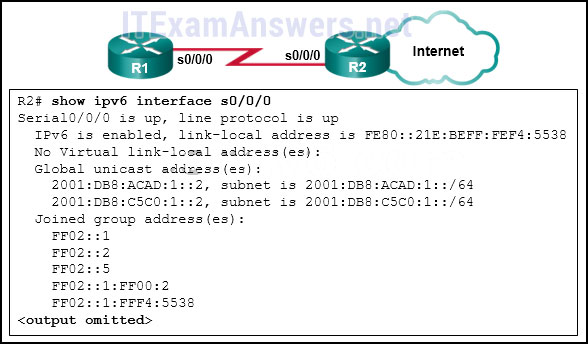

- 2001:DB8:C5C0:1::2
- FF02::5
- 2001:DB8:ACAD:1::2
- FE80::21E:BEFF:FEF4:5538*
134. Refer to the exhibit. What will Router1 do if it receives packets that are destined to network 2001:db8:11:100::/64?
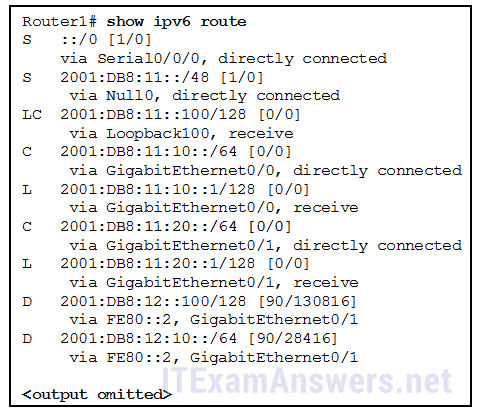

- send the packets out interface Serial 0/0/0
- drop the packets*
- send the packets out interface GigabitEthernet 0/0
- forward the packets to the gateway of last resort
135. Match the order in which the link-state routing process occurs on a router. (Not all options are used.)
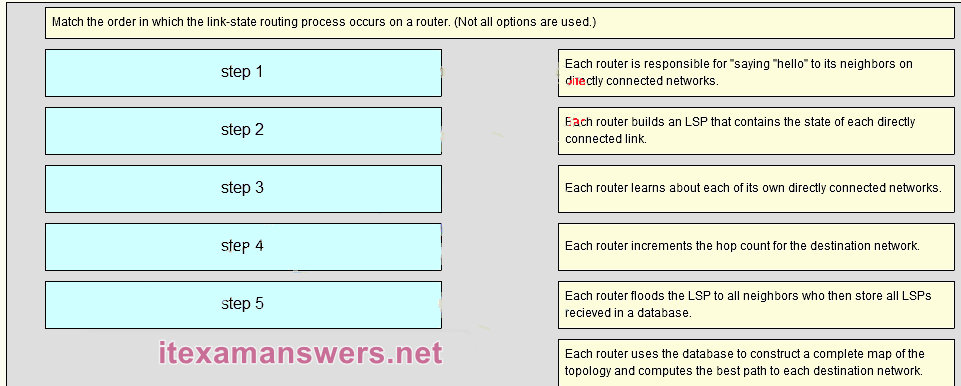
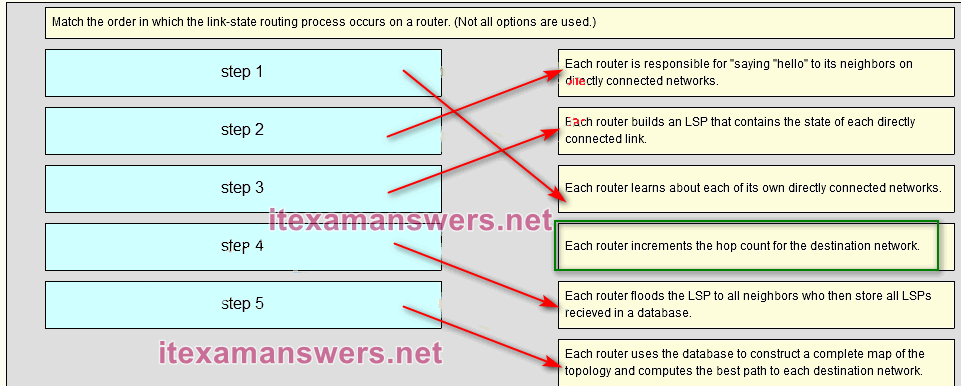
Each router learns about its own directly connected networks. => Step 1
Each router is responsible for “saying hello” to its neighbors on directly connected networks. => Step 2
Each router builds a Link-State Packet (LSP) containing the state of each directly connected link => Step 3
Each router floods the LSP to all neighbors, who then store all LSPs received in a database => Step 4
Each router uses the database to construct a complete map of the topology and computes the best => Step 5


Each router learns about its own directly connected networks. => Step 1
Each router is responsible for “saying hello” to its neighbors on directly connected networks. => Step 2
Each router builds a Link-State Packet (LSP) containing the state of each directly connected link => Step 3
Each router floods the LSP to all neighbors, who then store all LSPs received in a database => Step 4
Each router uses the database to construct a complete map of the topology and computes the best => Step 5
136. Match the description to the term. (Not all options are used.)
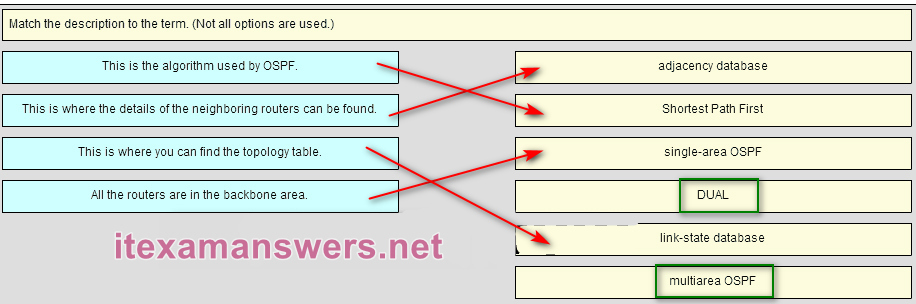
Place the options in the following order:adjacency database => This is where the details of the neighboring routers can be found.
Shortest Path First => This is the algorithm used by OSPF.
Single-area OSPF => All the routers are in the backbone area.
– not scored –
link-state database => This is where you can find the topology table.
– not scored –


Place the options in the following order:adjacency database => This is where the details of the neighboring routers can be found.
Shortest Path First => This is the algorithm used by OSPF.
Single-area OSPF => All the routers are in the backbone area.
– not scored –
link-state database => This is where you can find the topology table.
– not scored –
137. Match the order of precedence to the process logic that an OSPFv3 network router goes through in choosing a router ID. (Not all options are used.)
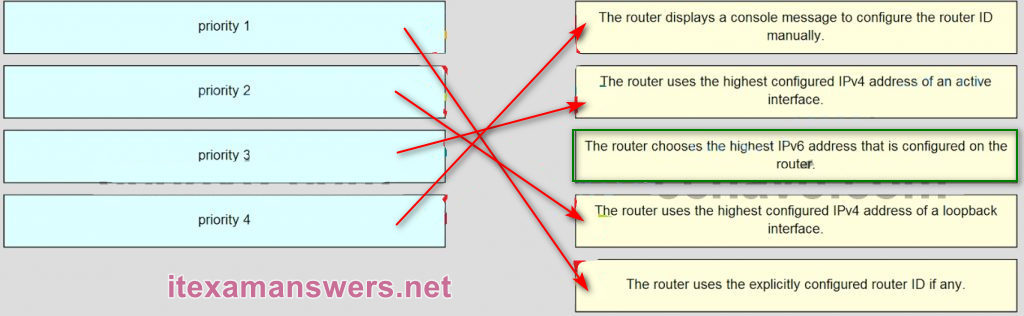 The router displays a console message to configure the router ID manually. => priority 4The router uses the highest configured IPv4 address of an active interface. => priority 3The router uses the highest configured IPv4 address of a loopback interface. => prority 2
The router displays a console message to configure the router ID manually. => priority 4The router uses the highest configured IPv4 address of an active interface. => priority 3The router uses the highest configured IPv4 address of a loopback interface. => prority 2

 The router displays a console message to configure the router ID manually. => priority 4The router uses the highest configured IPv4 address of an active interface. => priority 3The router uses the highest configured IPv4 address of a loopback interface. => prority 2
The router displays a console message to configure the router ID manually. => priority 4The router uses the highest configured IPv4 address of an active interface. => priority 3The router uses the highest configured IPv4 address of a loopback interface. => prority 2
The router uses the explicitly configured router ID if any. => priority 1
138. Which statement is true about the port roles of the 802.1w Rapid Spanning Tree Protocol?
- Ports are manually configured to be in the designated role.
- Cisco-proprietary enhancements to the legacy 802.1D, such as UplinkFast and BackboneFast, are compatible with RSTP.*
- An alternate or backup port can immediately change to a forwarding state without waiting for the network to converge.
- It takes an edge port 15 seconds to go from blocking to forwarding.
139. Which protocol does EIGRP use for the delivery and reception of EIGRP packets?
- Reliable Transport Protocol (RTP)*
- Transmission Control Protocol (TCP)
- ICMP Router Discovery Protocol (IRDP)
- User Datagram Protocol (UDP)
Older Version:
140. What are three access layer switch features that are considered when designing a network? (Choose three.)
- broadcast traffic containment
- failover capability
- forwarding rate*
- port density*
- Power over Ethernet*
- speed of convergence
141. In a large enterprise network, which two functions are performed by routers at the distribution layer? (Choose two.)
- connect remote networks*
- provide Power over Ethernet to devices
- connect users to the network
- provide data traffic security*
- provide a high-speed network backbone
142. Refer to the exhibit. Which switch will be the root bridge after the election process is complete?
- S1
- S2*
- S3
- S4
143. Refer to the exhibit. A network administrator is configuring PVST+ for the three switches. What will be a result of entering these commands?
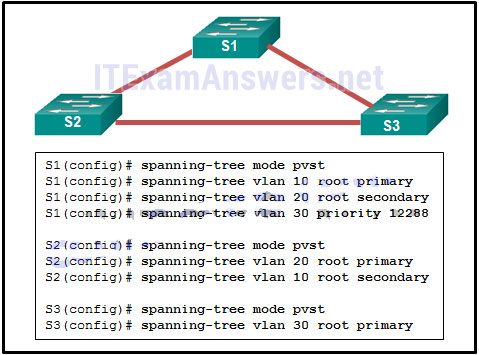

- S1 will set the priority value for VLAN 10 to 0.
- S2 will set the priority value for VLAN 10 to 24576.
- S3 will set the priority value for VLAN 30 to 8192.*
- S1 will set the priority value for VLAN 20 to 24596.
144. Refer to the exhibit. Which destination MAC address is used when frames are sent from the workstation to the default gateway?
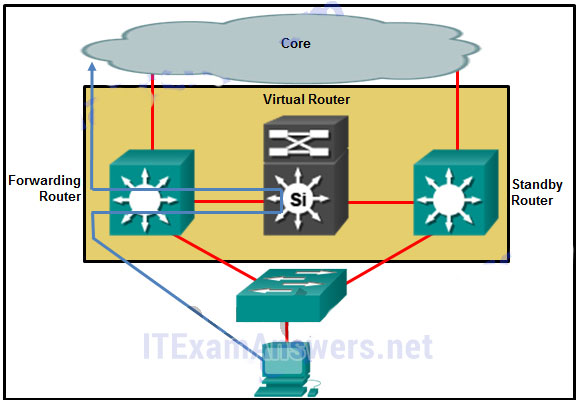

- MAC address of the forwarding router
- MAC addresses of both the forwarding and standby routers
- MAC address of the standby router
- MAC address of the virtual router*
145. Which function is provided by EtherChannel?
- spreading traffic across multiple physical WAN links
- dividing the bandwidth of a single link into separate time slots
- enabling traffic from multiple VLANs to travel over a single Layer 2 link
- creating one logical link by using multiple physical links between two LAN switches *
146. Which two channel group modes would place an interface in a negotiating state using PAgP? (Choose two.)
- desirable*
- on
- active
- auto*
- passive
147. What are two requirements to be able to configure an EtherChannel between two switches? (Choose two.)
- The interfaces that are involved need to be contiguous on the switch.
- All the interfaces need to work at the same speed. *
- All the interfaces need to be working in the same duplex mode.*
- All interfaces need to be assigned to different VLANs.
- Different allowed ranges of VLANs must exist on each end.
148. Refer to the exhibit. Which two conclusions can be drawn from the output? (Choose two.)
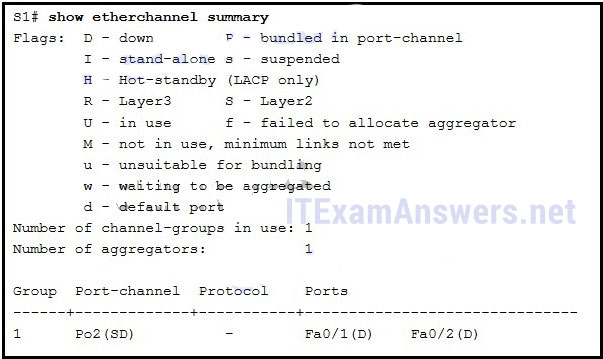

- The EtherChannel is down. *
- The port channel ID is 2.*
- The port channel is a Layer 3 channel.
- The bundle is fully operational.
- The load-balancing method used is source port to destination port.
149. What two conditions have to be met in order to form a cluster that includes 5 access points? (Choose two.)
- Clustering mode must be enabled on the APs.*
- At least two controllers are needed to form the cluster.
- The APs have to be connected on the same network segment.*
- The APs must all be configured to use different radio modes.
- The APs must use different cluster names.
150. A remote classroom can successfully access video-intensive streaming lectures via wired computers. However, when an 802.11n wireless access point is installed and used with 25 wireless laptops to access the same lectures, poor audio and video quality is experienced. Which wireless solution would improve the performance for the laptops?
- Decrease the power of the wireless transmitter.
- Add another access point.*
- Upgrade the access point to one that can route.
- Adjust the wireless NICs in the laptops to operate at 10GHz to be compatible with 802.11n.
151. Which wireless network topology is being configured by a technician who is installing a keyboard, a mouse, and headphones, each of which uses Bluetooth?
- ad hoc mode*
- hotspot
- infrastructure mode
- mixed mode
152. What are the two methods that are used by a wireless NIC to discover an AP? (Choose two.)
- sending an ARP request
- delivering a broadcast frame
- transmitting a probe request*
- initiating a three-way handshake
- receiving a broadcast beacon frame*
153. At a local college, students are allowed to connect to the wireless network without using a password. Which mode is the access point using?
- network
- open*
- passive
- shared-key
154. Which wireless encryption method is the most secure?
- WPA
- WEP
- WPA2 with TKIP
- WPA2 with AES*
155. Users on an IEEE 801.11n network are complaining of slow speeds. The network administrator checks the AP and verifies it is operating properly. What can be done to improve the wireless performance in the network?
- Split the wireless traffic between the 802.11n 2.4 GHz band and the 5 GHz band.*
- Change the authentication method on the AP.
- Switch to an 802.11g AP.
- Set the AP to mixed mode.
156. A network engineer is implementing security on all company routers. Which two commands must be issued to force authentication via the password 1C34dE for all OSPF-enabled interfaces in the backbone area of the company network? (Choose two.)
- ip ospf message-digest-key 1 md5 1C34dE*
- area 1 authentication message-digest
- username OSPF password 1C34dE
- enable password 1C34dE
- area 0 authentication message-digest*
157. Refer to the exhibit. When the show ip ospf neighbor command is given from the R1# prompt, no output is shown. However, when the show ip interface brief command is given, all interfaces are showing up and up. What is the most likely problem?
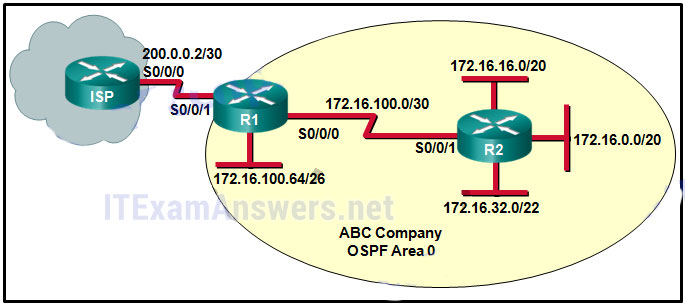

- R2 has not brought the S0/0/1 interface up yet.
- R1 or R2 does not have a loopback interface that is configured yet.
- The ISP has not configured a static route for the ABC Company yet.
- R1 or R2 does not have a network statement for the 172.16.100.0 network.*
- R1 has not sent a default route down to R2 by using the default-information originate command.
158. What are two methods to make the OSPF routing protocol more secure? (Choose two.)
- Use only OSPFv3.
- Use MD5 authentication.*
- Use the enable secret command.
- When feasible, create a VPN tunnel between each OSPF neighbor adjacency.
- Use the passive-interface command on LAN interfaces that are connected only to end-user devices.*
159. A network engineer is troubleshooting a single-area OSPFv3 implementation across routers R1, R2, and R3. During the verification of the implementation, it is noted that the routing tables on R1 and R2 do not include the entry for a remote LAN on R3. Examination of R3 shows the following:
1.that all interfaces have correct addressing
2.that the routing process has been globally configured
3.that correct router adjacencies have formed
What additional action taken on R3 could solve the problem?
1.that all interfaces have correct addressing
2.that the routing process has been globally configured
3.that correct router adjacencies have formed
What additional action taken on R3 could solve the problem?
- Enable the OSPFv3 routing process on the interface connected to the remote LAN.*
- Use the network command to configure the LAN network under the global routing process.
- Force DR/BDR elections to occur where required.
- Restart the OPSFv3 routing process.
160. Refer to the exhibit. A network technician is troubleshooting missing OSPFv3 routes on a router. What is the cause of the problem based on the command output?
- There is a problem with the OSPFv3 adjacency between the local router and the router that is using the neighbor ID 2.2.2.2.*
- The local router has formed complete neighbor adjacencies, but must be in a 2WAY state for the router databases to be fully synchronized.
- The dead time must be higher than 30 for all routers to form neighbor adjacencies.
- The neighbor IDs are incorrect. The interfaces must use only IPv6 addresses to ensure fully synchronized routing databases.
161. When does an OSPF router become an ABR?
- when the router has interfaces in different areas*
- when the router is configured as an ABR by the network administrator
- when the router has the highest router ID
- when the router has an OSPF priority of 0
162. Which type of OSPF LSA represents an external route and is propagated across the entire OSPF domain?
- type 1
- type 2
- type 3
- type 4
- type 5*
163. Refer to the exhibit. What can be concluded about network 192.168.1.0 in the R2 routing table?

- This network has been learned from an internal router within the same area.
- This network was learned through summary LSAs from an ABR.*
- This network is directly connected to the interface GigabitEthernet0/0.
- This network should be used to forward traffic toward external networks.
164. Refer to the exhibit. A company has migrated from single area OSPF to multiarea. However, none of the users from network 192.168.1.0/24 in the new area can be reached by anyone in the Branch1 office. From the output in the exhibit, what is the problem?
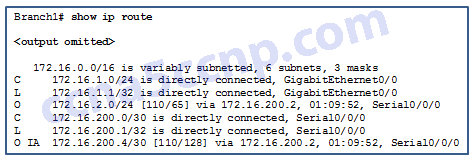
- There are no interarea routes in the routing table for network 192.168.1.0.*
- The OSPF routing process is inactive.
- The link to the new area is down.
- The router has not established any adjacencies with other OSPF routers.
165. When are EIGRP update packets sent?
- only when necessary*
- when learned routes age out
- every 5 seconds via multicast
- every 30 seconds via broadcast
166. Refer to the exhibit. If router B is to be configured for EIGRP AS 100, which configuration must be entered?
- B(config-router)# network 192.168.10.4 0.0.0.3
B(config-router)# network 192.168.10.8 0.0.0.3 - B(config-router)# network 192.168.10.4 0.0.0.3
B(config-router)# network 192.168.10.8 0.0.0.3
B(config-router)#network 192.168.10.128 0.0.0.63 - B(config-router)# network 192.168.10.4 255.255.255.248
B(config-router)# network 192.168.10.8 255.255.255.248
B(config-router)#network 192.168.10.128 255.255.255.192 - B(config-router)# network 192.168.10.0 255.255.255.0
B(config-router)# network 192.168.10.4 0.0.0.3
B(config-router)# network 192.168.10.8 0.0.0.3
B(config-router)# network 192.168.10.64 0.0.0.63
B(config-router)# network 192.168.10.128 0.0.0.63
B(config-router)# network 192.168.10.192 0.0.0.63 - B(config-router)# network 192.168.10.0 0.0.0.255
167. An administrator issues the router eigrp 100 command on a router. What is the number 100 used for?
- as the autonomous system number*
- as the number of neighbors supported by this router
- as the length of time this router will wait to hear hello packets from a neighbor
- as the maximum bandwidth of the fastest interface on the router
168. A network administrator wants to verify the default delay values for the interfaces on an EIGRP-enabled router. Which command will display these values?
- show ip protocols
- show running-config
- show interfaces*
- show ip route
169. Which two parameters does EIGRP use by default to calculate the best path? (Choose two.)
- delay*
- MTU
- reliability
- transmit and receive load
- bandwidth*
170. Refer to the exhibit. A network administrator issues the show ipv6 eigrp neighbors command. Which conclusion can be drawn based on the output?
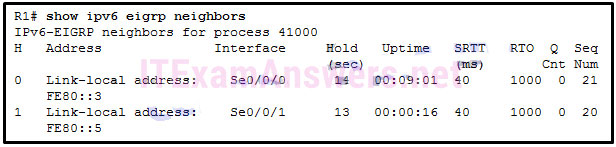

- The link-local addresses of neighbor routers interfaces are configured manually.*
- R1 has two neighbors. They connect to R1 through their S0/0/0 and S0/0/1 interfaces.
- The neighbor with the link-local address FE80::5 is the first EIGRP neighbor that is learned by R1.
- If R1 does not receive a hello packet from the neighbor with the link-local address FE80::5 in 2 seconds, it will declare the neighbor router is down.
171. When a Cisco router is configured with fast-switching, how are packets distributed over equal-cost paths?
- on a per-packet basis
- on a per-interface basis
- on a per-path-load basis
- on a per-destination basis*
172. Refer to the exhibit. Router CiscoVille has been partially configured for EIGRP authentication. What is missing that would allow successful authentication between EIGRP neighbors?
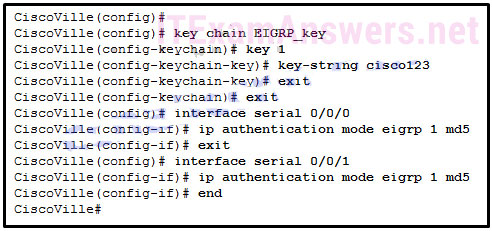

- The interfaces that will use EIGRP authentication must be specified.
- A username and password must be configured.
- The keychain for EIGRP authentication must be configured on the interfaces. *
- The CiscoVille router requires a second keychain to function correctly when using two interfaces for EIGRP authentication.
173. Refer to the exhibit. Routers R1 and R2 are directly connected via their serial interfaces and are both running the EIGRP routing protocol. R1 and R2 can ping the directly connected serial interface of their neighbor, but they cannot form an EIGRP neighbor adjacency. What action should be taken to solve this problem?
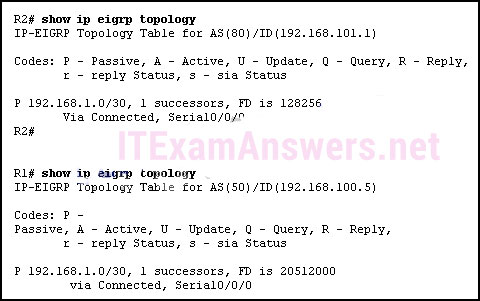

- Enable the serial interfaces of both routers.
- Configure EIGRP to send periodic updates.
- Configure the same hello interval between the routers.
- Configure both routers with the same EIGRP autonomous system number.*
174. Which two conditions should the network administrator verify before attempting to upgrade a Cisco IOS image using a TFTP server? (Choose two.)
- Verify the name of the TFTP server using the show hosts command.
- Verify that the TFTP server is running using the tftpdnld command.
- Verify that the checksum for the image is valid using the show version command.
- Verify connectivity between the router and TFTP server using the ping command. *
- Verify that there is enough flash memory for the new Cisco IOS image using the show flash command.*
175. Which requirement should be checked before a network administrator performs an IOS image upgrade on a router?
- The FTP server is operational.
- The old IOS image file has been deleted.
- There is sufficient space in flash memory.*
- The desired IOS image file has been downloaded to the router.
176. Refer to the exhibit. A network administrator is attempting to upgrade the IOS system image on a Cisco 2901 router. After the new image has been downloaded and copied to the TFTP server, what command should be issued on the router before the IOS system image is upgraded on the router?
- show license all
- ping 10.10.10.1
- copy tftp: flash0:
- ping 10.10.10.2*
177. What is the purpose of the Cisco PAK?
- It is a key for enabling an IOS feature set.*
- It is a proprietary encryption algorithm.
- It is a compression file type used when installing IOS 15 or an IOS upgrade.
- It is a way to compress an existing IOS so that a newer IOS version can be co-installed on a router.
178. Which Cisco IOS Software Release 15.0 technology pack is shipped with a permanent license on all Cisco ISR G2 devices?
- IPBase*
- DATA
- Unified Communications
- Security
179. A network administrator issues the command R1(config)# license boot module c1900 technology-package securityk9 on a router. What is the effect of this command?
- The IOS will prompt the user to reboot the router.
- The features in the Security package are available immediately.
- The IOS will prompt the user to provide a UDI in order to activate the license.
- The Evaluation Right-To-Use license for the Security technology package is activated.*
180. What two license states would be expected on a new Cisco router once the license has been activated? (Choose two.)
- License Type: ipbasek9
- License Type: Permanent*
- License Type: Temporary
- License State: Active, In Use*
- License State: Active, Registered
- License State: On
181. Fill in the blank.
The backbone area interconnects with all other OSPF area types.
The backbone area interconnects with all other OSPF area types.
182. What is a difference between the Cisco IOS 12 and IOS 15 versions?
- The IOS 12 version has commands that are not available in the 15 version.
- The IOS version 15 license key is unique to each device, whereas the IOS version 12 license key is not device specific.*
- Every Cisco ISR G2 platform router includes a universal image in the IOS 12 versions, but not the IOS 15 versions.
- IOS version 12.4(20)T1 is a mainline release, whereas IOS version 15.1(1)T1 is a new feature release.
183. A network administrator issues the command R1(config)# license boot module c1900 technology-package securityk9 on a router. What is the effect of this command?
- The IOS will prompt the user to reboot the router.
- The features in the Security package are available immediately.
- The IOS will prompt the user to provide a UDI in order to activate the license.
- The Evaluation Right-To-Use license for the Security technology package is activated.*
184. A network administrator is troubleshooting slow performance in a Layer 2 switched network. Upon examining the IP header, the administrator notices that the TTL value is not decreasing. Why is the TTL value not decreasing?
- This is the normal behavior for a Layer 2 network.*
- The MAC address table is full.
- The VLAN database is corrupt.
- The inbound interface is set for half duplex.
185. An STP instance has failed and frames are flooding the network. What action should be taken by the network administrator?
- A response from the network administrator is not required because the TTL field will eventually stop the frames from flooding the network.
- Spanning tree should be disabled for that STP instance until the problem is located.
- Broadcast traffic should be investigated and eliminated from the network.
- Redundant links should be physically removed until the STP instance is repaired.*
186. A network engineer is configuring a LAN with a redundant first hop to make better use of the available network resources. Which protocol should the engineer implement?
- FHRP
- GLBP*
- HSRP
- VRRP
187. A network engineer is troubleshooting a newly deployed wireless network that is using the latest 802.11 standards. When users access high bandwidth services such as streaming video, the wireless network performance is poor. To improve performance the network engineer decides to configure a 5 Ghz frequency band SSID and train users to use that SSID for streaming media services. Why might this solution improve the wireless network performance for that type of service?
- The 5 GHz band has a greater range and is therefore likely to be interference-free.
- Requiring the users to switch to the 5 GHz band for streaming media is inconvenient and will result in fewer users accessing these services.
- The 5 GHz band has more channels and is less crowded than the 2.4 GHz band, which makes it more suited to streaming multimedia.*
- The only users that can switch to the 5 GHz band will be those with the latest wireless NICs, which will reduce usage.
188. What method of wireless authentication is dependent on a RADIUS authentication server?
- WEP
- WPA Personal
- WPA2 Personal
- WPA2 Enterprise*
189. Refer to the exhibit. What two pieces of information could be determined by a network administrator from this output? (Choose two.)


- R1 is participating in multiarea OSPF.*
- The OSPF process number that is being used is 0.
- Interface Fa0/1 is not participating in the OSPF process. *
- R1 is the distribution point for the routers that are attached to the 10.0.0.4 network.*
- The metric that will be installed in the routing table for the 10.0.0.0 route will be 65 (64+1).
190. What is a wireless modulation technique used by 802.11 WLAN standards that can implement MIMO?
- BSS
- DSSS
- FHSS
- OFDM*
191. A network administrator in a branch office is configuring EIGRP authentication between the branch office router and the headquarters office router. Which security credential is needed for the authentication process?
- a randomly generated key with the crypto key generate rsa command
- the username and password configured on the headquarters office router
- the hostname of the headquarters office router and a common password
- a common key configured with the key-string command inside a key chain*
192. For troubleshooting missing EIGRP routes on a router, what three types of information can be collected using the show ip protocols command? (Choose three.)
- any interfaces that are enabled for EIGRP authentication
- any interfaces on the router that are configured as passive*
- the IP addresses that are configured on adjacent routers
- any ACLs that are affecting the EIGRP routing process *
- networks that are unadvertised by the EIGRP routing protocol*
- the local interface that is used to establish an adjacency with EIGRP neighbors
193. Which port role is assigned to the switch port that has the lowest cost to reach the root bridge?
- root port*
- non-designated port
- designated port
- disabled port
194. Refer to the exhibit. A network administrator is attempting to upgrade the IOS system image on a Cisco 2901 router. After the new image has been downloaded and copied to the TFTP server, what command should be issued on the router before the IOS system image is upgraded on the router?
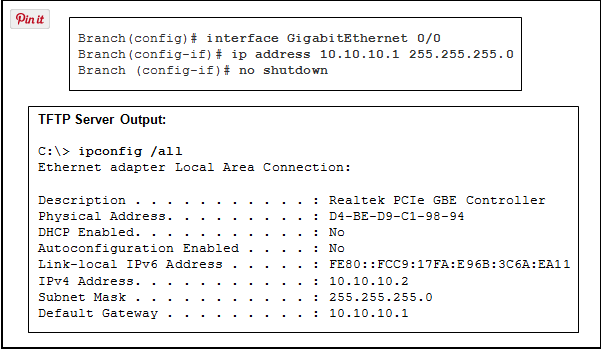

- dir flash:
- ping 10.10.10.1
- copy tftp: flash0:
- ping 10.10.10.2*
195. Which technology is an open protocol standard that allows switches to automatically bundle physical ports into a single logical link?
- Multilink PPP
- DTP
- LACP*
- PAgP
196. Refer to the exhibit. Based on the command output shown, what is the status of the EtherChannel?
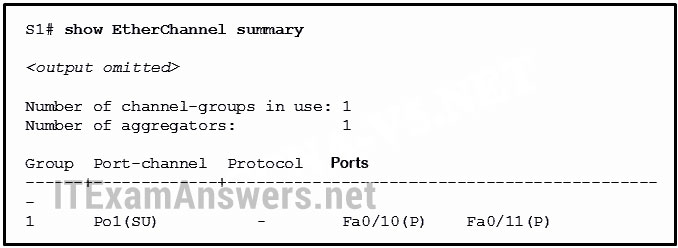

- The EtherChannel is dynamic and is using ports Fa0/10 and Fa0/11 as passive ports.
- The EtherChannel is down as evidenced by the protocol field being empty.
- The EtherChannel is partially functional as indicated by the P flags for the FastEthernet ports.
- The EtherChannel is in use and functional as indicated by the SU and P flags in the command output.*
197. If a company wants to upgrade a Cisco 2800 router from IOS 12.4T, what IOS should be recommended for a stable router platform?
- 12.5T
- 13.1T
- 14.0
- 15.1M*
198. Fill in the blank.
EIGRP keeps feasible successor routes in the topology table.
EIGRP keeps feasible successor routes in the topology table.
199. Fill in the blank. Use the acronym. Which encryption protocol is used by the WPA2 shared key authentication technique?
AES
AES
200. Which action should be taken when planning for redundancy on a hierarchical network design?
- immediately replace a non-functioning module, service or device on a network
- continually purchase backup equipment for the network
- implement STP portfast between the switches on the network
- add alternate physical paths for data to traverse the network*
201. Refer to the exhibit. Why did R1 and R2 not establish an adjacency?
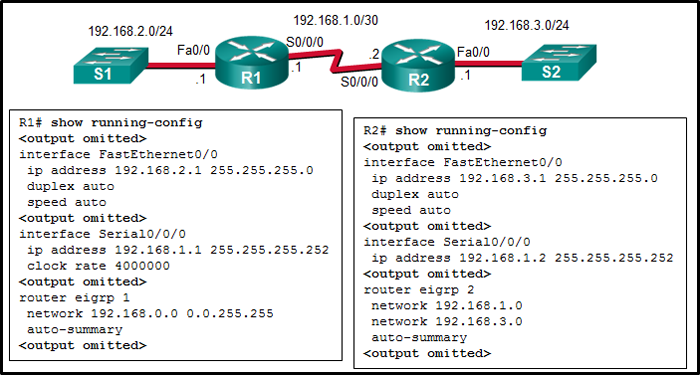
- R1 S0/0/0 and R2 S0/0/0 are on different networks.
- The AS number must be the same on R1 and R2.*
- The link-local address must be the same on both routers.
- The no shutdown command is misapplied on both routers.
- The router ID must be the same on both routers.
202. A network administrator issues the command R1(config)# license boot module c1900 technology-package securityk9 on a router. What is the effect of this command?
- The IOS will prompt the user to reboot the router.
- The features in the Security package are available immediately.
- The IOS will prompt the user to provide a UDI in order to activate the license.
- The Evaluation Right-To-Use license for the Security technology package is activated.*
203. Match the CLI command prompt with the command or response entered when backing up a Release 15 IOS image to an IPv6 TFTP server. (Not all options are used.)
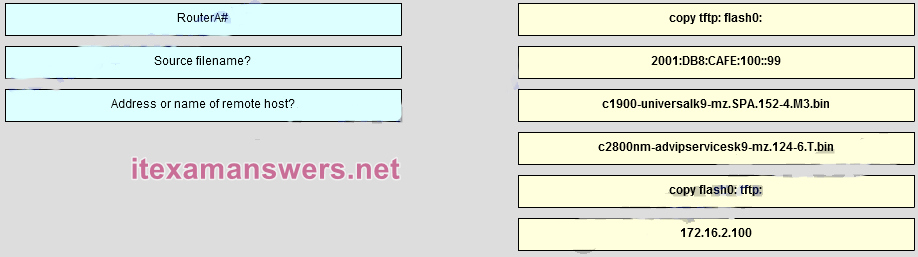
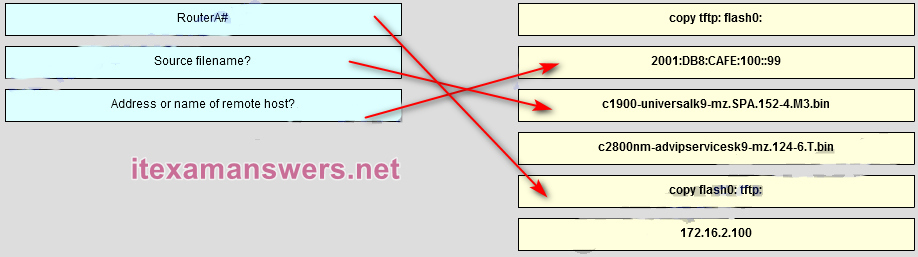
RouterA# -> copy flash0:tftp:
Source Filename? -> C1900-universalk9-m.SPA.152-4.M3.bin
Address or name of remote host ->2001:DB8:CAFE:100::9


RouterA# -> copy flash0:tftp:
Source Filename? -> C1900-universalk9-m.SPA.152-4.M3.bin
Address or name of remote host ->2001:DB8:CAFE:100::9
204. Refer to the exhibit. An administrator attempts to configure EIGRP for IPv6 on a router and receives the error message that is shown. Which command must be issued by the administrator before EIGRP for IPv6 can be configured?


- eigrp router-id 100.100.100.100
- no shutdown
- ipv6 eigrp 100
- ipv6 cef
- ipv6 unicast-routing*
205. Which technological factor determines the impact of a failure domain?
- the forwarding rate of the switches used on the access layer
- the number of layers of the hierarchical network
- the role of the malfunctioning device*
- the number of users on the access layer
206. What are two differences between the Cisco IOS 12 and IOS 15 versions? (Choose two.)
- Every Cisco ISR G2 platform router includes a universal image in the IOS 12 versions, but not the IOS 15 versions.
- The IOS version 15 license key is unique to each device, whereas the IOS version 12 license key is not device specific.*
- The IOS 12 version has two trains that occur simultaneously, whereas the IOS 15 version still has two trains, but the versions occur in a single sequential order.
- The IOS 12 version has commands that are not available in the 15 version.
- IOS version 12.4(20)T1 is a mainline release, whereas IOS version 15.1(1)T1 is a new feature release.*
207. Refer to the exhibit. What are two results of issuing the displayed commands on S1, S2, and S3? (Choose two.)


- S3 can be elected as a secondary bridge.
- S2 can become root bridge if S3 fails.
- S1 will automatically adjust the priority to be the lowest.*
- S2 can become root bridge if S1 fails.*
- S1 will automatically adjust the priority to be the highest.
208. Which action should be taken when planning for redundancy on a hierarchical network design?
- add alternate physical paths for data to traverse the network
- continually purchase backup equipment for the network*
- immediately replace a non-functioning module, service or device on a network
- implement STP portfast between the switches on the network
209. Fill in the blank. Use the acronym. Which encryption protocol is used by the WPA2 shared key authentication technique?
AES
AES
210. Refer to the exhibit. Interface FastEthernet 0/1 on S1 is connected to Interface FastEthernet 0/1 on S2, and Interface FastEthernet 0/2 on S1 is connected to Interface FastEthernet 0/2 on S2. What are two errors in the present EtherChannel configurations? (Choose two.)
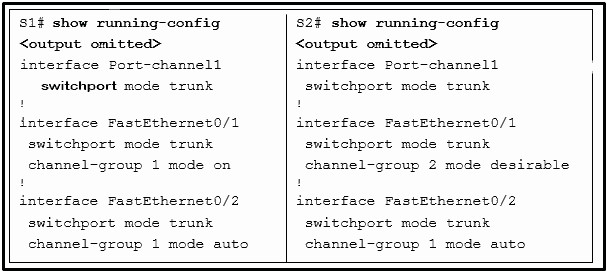

- Desirable mode is not compatible with on mode.
- The trunk mode is not allowed for EtherChannel bundles.
- Two auto modes cannot form a bundle.*
- The channel group is inconsistent.*
- The interface port channel ID should be different in both switches.
211. Launch PT Hide and Save PT
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
Which message was displayed on the web server?
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
Which message was displayed on the web server?
- Work done!
- Congratulations!
- Wonderful work!
- You’ve made it!*
212. A network administrator has configured an EtherChannel between two switches that are connected via four trunk links. If the physical interface for one of the trunk links changes to a down state, what happens to the EtherChannel?
- Spanning Tree Protocol will recalculate the remaining trunk links.
- The EtherChannel will remain functional.*
- The EtherChannel will transition to a down state.
- Spanning Tree Protocol will transition the failed physical interface into forwarding mode.
213. What are two requirements when using out-of-band configuration of a Cisco IOS network device? (Choose two.)
- Telnet or SSH access to the device
- a connection to an operational network interface on the device
- a direct connection to the console or AUX port*
- a terminal emulation client*
- HTTP access to the device
214. A network administrator issues the command R1(config)# license boot module c1900 technology-package securityk9 on a router. What is the effect of this command?
- The IOS will prompt the user to provide a UDI in order to activate the license.
- The IOS will prompt the user to reboot the router.
- The features in the Security package are available immediately.
- The Evaluation Right-To-Use license for the Security technology package is activated.*
215. A router has been removed from the network for maintenance. A new Cisco IOS software image has been successfully downloaded to a server and copied into the flash of the router. What should be done before placing the router back into service?
- Delete the previous version of the Cisco IOS software from flash.
- Copy the running configuration to NVRAM.
- Back up the new image.
- Restart the router and verify that the new image starts successfully.*
216. Refer to the exhibit. Why did R1 and R2 not establish ad adjacency?
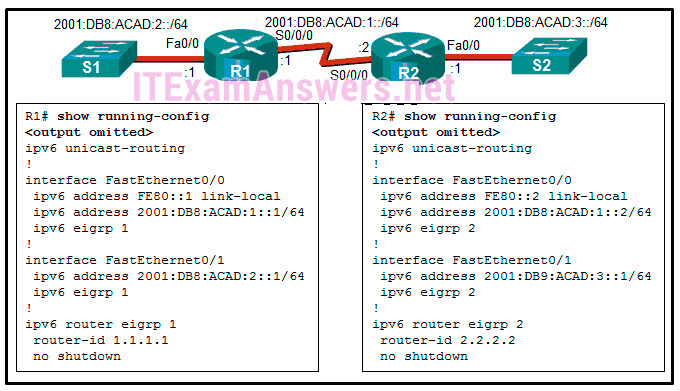

- The link-local address must be the same on both routers.
- The AS number must be the same on R1 and R2.*
- R1 S0/0/0 and R2 S0/0/0 are on different networks.
- The no shutdown command is misapplied on both routers.
- The router ID must be the same on both routers.
217. Refer to the exhibit. Match the description to the corresponding value used by the DUAL FSM. (Not all options are used.)
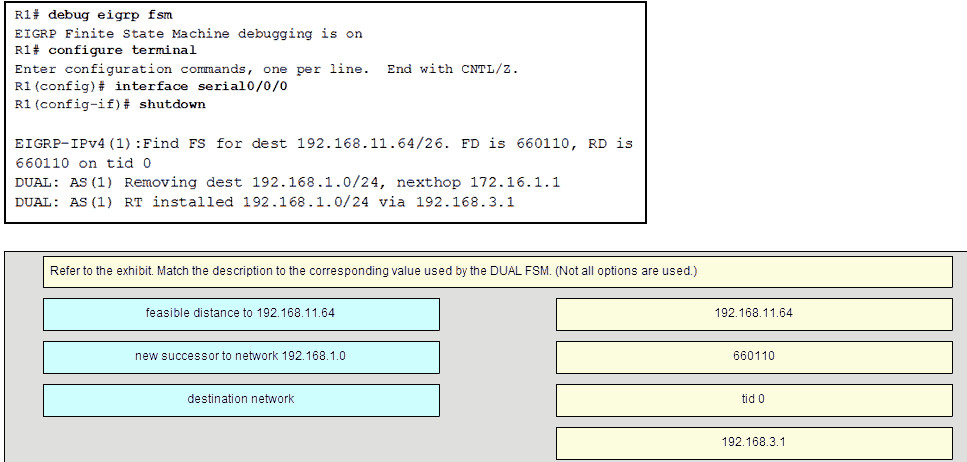
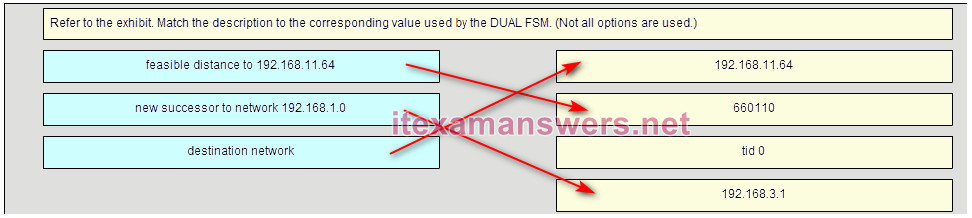
feasible distance to 192.168.11.64 => 660110
new successor to network 192.168.1.0 => 192.168.3.1
destination network => 192.168.11.64


feasible distance to 192.168.11.64 => 660110
new successor to network 192.168.1.0 => 192.168.3.1
destination network => 192.168.11.64
218. What are two reasons to implement passive interfaces in the EIGRP configuration of a Cisco router? (Choose two.)
- to provide increased network security*
- to shut down unused interfaces
- to exclude interfaces from load balancing
- to mitigate attacks coming from the interfaces
- to avoid unnecessary update traffic *
219. Fill in the blank. Do not use abbreviations.
The spanning-tree “mode rapid-pvst” global configuration command is used to enable Rapid PVST+.
The spanning-tree “mode rapid-pvst” global configuration command is used to enable Rapid PVST+.
220. A WLAN user wants to allocate an optimal amount of bandwidth to a specific online game. What is a Linksys Smart Wi-Fi tool that will allow the user to do this?
- WidgetsSpeed
- TestMedia
- Prioritization
- Bandwidth Prioritization*
221. Fill in the blank.
EIGRP keeps feasible successor routes in the “topology” table.
EIGRP keeps feasible successor routes in the “topology” table.
222. What type of OSPF IPv4 route is indicated by a route table entry descriptor of O E1?
- an intra-area route that is advertised by the DR
- a summary route that is advertised by an ABR
- a directly connected route that is associated with an Ethernet interface
- an external route that is advertised by an ASBR*
223. What is the purpose of a Cisco IOS 15 EM release?
- It specifies advanced IP services features such as advanced security and service provider packages.
- It provides premium packages and enables additional IOS software feature combinations that address more complex network requirements.
- It provides regular bug fix maintenance rebuilds, plus critical fix support for network-affecting bugs.*
- It is used for long-term maintenance, enabling customers to qualify, deploy, and remain on the release for an extended period.
224. A network administrator is analyzing first -hop router redundancy protocols. What is characteristic of VRRPv3?
- INTEROPERABILITY IN MULTI-VENDOR ENVIRONMENTS*
- VRRPv3 SUPPORTS USAGE OF IPv4 and IPv6*
- IMPROVE SCALABILITY THROUGH USE OF VRRS PATHWAYS*
- so judging from the options given it will be supports both IPv6 and IPv4 addressing
225. What occurs when authentication is configured on an EIGRP router?
- After EIGRP authentication has been configured, the router must be rebooted to be able to reestablish adjacencies.
- If adjacencies are displayed after the use of the show ipv6 eigrp neighbors command, then EIGRP authentication was successful.*
- Only one router is required to be configured for EIGRP authentication.
- If only one router has been configured for EIGRP authentication, any prior adjacencies will remain intact.
226. Refer to the exhibit. A network administrator is configuring PVST+ for the three switches.
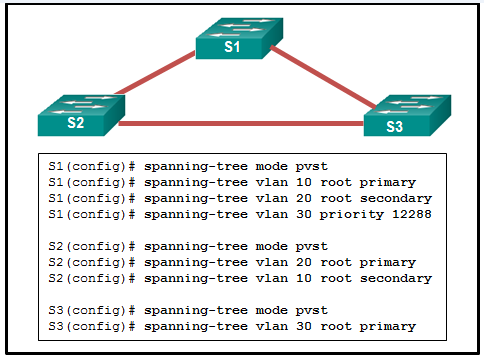
What will be a result of entering these commands?

What will be a result of entering these commands?
- S2 will set the priority value for VLAN 10 to 24576
- S1 will set the priority value for VLAN 20 to 24596
- S3 will set the priority value for VLAN 30 to 8192*
- S1 will set the priority value for VLAN 10 to 0
227. What are two drawbacks to turning spanning tree off and having multiple paths through the Layer 2 switch network? (Choose two.)
- Broadcast frames are transmitted indefinitely.*
- Port security shuts down all of the port that attached devices.The switch acts like a hub.
- The Mac address table becomes unstable.*
- Port security becomes unstable.
228. Match the OSPF router type description with its name
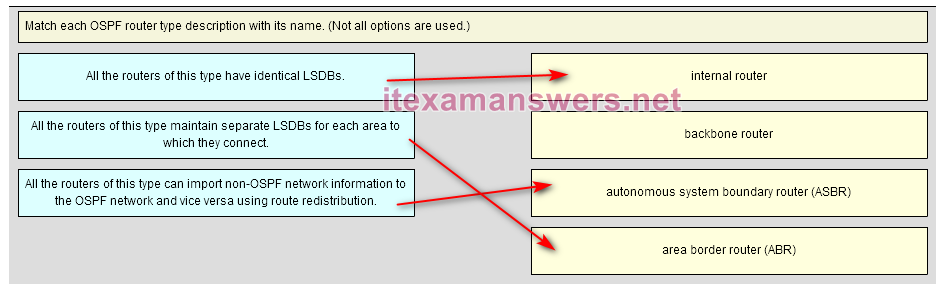 Internal routers -> All the router of this type have identical LSDBs.Area border routers (ABR) -> All the routers of this type maintain separate LSDBs for each area to which they connect.Autonomous System Boundary Routers (ASBR) -> All the router of this type can import non-OSPF network information to the OSPF network and vice versa using route redistribution.
Internal routers -> All the router of this type have identical LSDBs.Area border routers (ABR) -> All the routers of this type maintain separate LSDBs for each area to which they connect.Autonomous System Boundary Routers (ASBR) -> All the router of this type can import non-OSPF network information to the OSPF network and vice versa using route redistribution.

 Internal routers -> All the router of this type have identical LSDBs.Area border routers (ABR) -> All the routers of this type maintain separate LSDBs for each area to which they connect.Autonomous System Boundary Routers (ASBR) -> All the router of this type can import non-OSPF network information to the OSPF network and vice versa using route redistribution.
Internal routers -> All the router of this type have identical LSDBs.Area border routers (ABR) -> All the routers of this type maintain separate LSDBs for each area to which they connect.Autonomous System Boundary Routers (ASBR) -> All the router of this type can import non-OSPF network information to the OSPF network and vice versa using route redistribution.
backbone router -> none
229. What is a requirement to configure a trunking EtherChannel between two switches?
- The participating interfaces must be on the same module on a switch.
- The participating interfaces must be physically contiguous on a switch.
- The participating interfaces must be assigned the same VLAN number on both switches.*
- The allowed range of VLANs must be the same on both switches.
230. What should be installed on a Cisco router as a prerequisite for installing the Data, Security, and Unified Communications licenses in IOS 15?
- the IP Base license*
- the Cisco License Manager
- the Enterprise Services package
- the Enterprise Base license
231. After implementing an IPv6 network, the administrator notices that the OSPFv3 process is not starting on the routers. What could be the problem?
- No router IDs are configured on the routers.*
- Authentication was not implemented between the routers.
- The routers were not configured with the network command.
- The routers are configured with the default priority.
232. Which statement describes the load balancing behavior of EIGRP?
- EIGRP for IPv6 supports unequal cost load balancing, but EIGRP for IPv4 does not.
- EIGRP for IPv4 supports unequal cost load balancing, but EIGRP for IPv6 does not.
- Neither EIGRP for IPv4 nor EIGRP for IPv6 support unequal cost load balancing.
- Both EIGRP for IPv4 and EIGRP for IPv6 support unequal cost load balancing.*
233. What is the purpose of the Cisco License Manager?
- It is a free software application that helps network administrators rapidly deploy multiple Cisco software licenses across their networks.*
- It is software that provides the Product Activation Key for the license and important information regarding the Cisco End User License Agreement.
- It is software that comes pre-installed with the software image and contains licenses for the customer-specified packages and features.
- It is a web-based portal for getting and registering individual software licenses.
234. While attending a conference, participants are using laptops for network connectivity. When a guest speaker attempts to connect to the network, the laptop fails to display any available wireless networks. The access point is probably operating in which mode?
- passive*
- mixed
- open
- active
235. Refer to the exhibit and the following error message from the SwB switch. 00:22:43: %SPANTREE-7-RECV_1Q_NON_TRUNK: Received 802.1Q BPDU on non trunk FastEthernet0/1 VLAN1
00:22:43: %SPANTREE-7-BLOCK_PORT_TYPE: Blocking FastEthernet0/1 on VLAN0001. Inconsistent port type.
Considering that the link between the two switches is good and the correct type, what could cause this error message?
00:22:43: %SPANTREE-7-BLOCK_PORT_TYPE: Blocking FastEthernet0/1 on VLAN0001. Inconsistent port type.
Considering that the link between the two switches is good and the correct type, what could cause this error message?
- The SwA port has IEEE 802.1Q trunking enabled and the SwB port has ISL trunking enabled.
- The SwA port is configured as a trunk port and the SwB port is configured as an access port.*
- The Spanning Tree Protocol has been disabled on both switches.
- The Spanning Tree Protocol has been disabled on one switch.
- The IEEE 802.1Q trunking port has a speed mismatch on one of the switches.
236. A network administrator is designing a wireless network for a new school building. The wireless network is for students using their own mobile devices. The network administrator wants to provide the most throughput possible even if the throughput is reduced by students using older devices. Which technology would be best in this situation?
- 802.11g*
- 802.11ac
- 802.11n
- 802.11ad
237. A company has deployed four 48-port access layer switches to a switch bock. For redundancy each access layer switch will connect to two distribution layer switches. Additionally, link aggregation will be used to combine 10 Gbps interfaces to form 20 Gbps trunk links form the access layer switches to the distribution layer switches. How many switch ports on the access layer switches will be available in the switch block to support end devices?
- 176*
- 184
- 188
- 192
238. What is a feature of the OSPF routing protocol?
- OSPF authentication is configured in the same way on IPV4 and IPV6 networks.
- The SPF algorithm chooses the best path based on 30-second updates.
- Routers can be grouped into autonomous systems to support a hierarchical system.
- It scales well in both small and large networks.*
239. Refer to the exhibit. If the switch has been configured for PVST+ mode, what command output would replace the question marks?
- pvst
- pvst+
- rstp
- ieee*