CCNA 2 R&S Essentials Practice Final v5.0 Exam Answers 2014
1
Which command would be best to use on an unused switch port if a company adheres to the best practices as recommended by Cisco?
Which command would be best to use on an unused switch port if a company adheres to the best practices as recommended by Cisco?
switchport port-security mac-address sticky
ip dhcp snooping
switchport port-security mac-address sticky mac-address
switchport port-security violation shutdown
shutdown*
ip dhcp snooping
switchport port-security mac-address sticky mac-address
switchport port-security violation shutdown
shutdown*
2

Refer to the exhibit. An administrator is trying to configure PAT on R1, but PC-A is unable to access the Internet. The administrator tries to ping a server on the Internet from PC-A and collects the debugs that are shown in the exhibit. Based on this output, what is most likely the cause of the problem?
The inside global address is not on the same subnet as the ISP.*
The NAT source access list matches the wrong address range.
The address on Fa0/0 should be 64.100.0.1.
The inside and outside NAT interfaces have been configured backwards.
The NAT source access list matches the wrong address range.
The address on Fa0/0 should be 64.100.0.1.
The inside and outside NAT interfaces have been configured backwards.
3
A small company has a web server in the office that is accessible from the Internet. The IP address 192.168.10.15 is assigned to the web server. The network administrator is configuring the router so that external clients can access the web server over the Internet. Which item is required in the NAT configuration?
A small company has a web server in the office that is accessible from the Internet. The IP address 192.168.10.15 is assigned to the web server. The network administrator is configuring the router so that external clients can access the web server over the Internet. Which item is required in the NAT configuration?
the ip nat inside source command to link the inside local and inside global addresses*
an ACL to identify the local IPv4 address of the web server
the keyword overload for the ip nat inside source command
an IPv4 address pool
an ACL to identify the local IPv4 address of the web server
the keyword overload for the ip nat inside source command
an IPv4 address pool
4
Which type of static route typically uses the distance parameter in the ip route global configuration command?
Which type of static route typically uses the distance parameter in the ip route global configuration command?
default static route
standard static route
summary static route
floating static route*
standard static route
summary static route
floating static route*
5
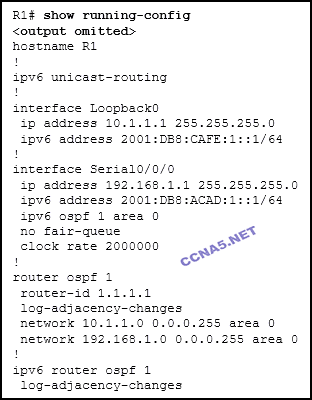
Refer to the exhibit. What address will be used as the router ID for the OSPFv3 process?
2001:DB8:CAFE:1::1
192.168.1.1
10.1.1.1*
1.1.1.1
2001:DB8:ACAD:1::1
192.168.1.1
10.1.1.1*
1.1.1.1
2001:DB8:ACAD:1::1
6
What is the order of packet types used by an OSPF router to establish convergence?
What is the order of packet types used by an OSPF router to establish convergence?
LSU, LSAck, Hello, DBD, LSR
Hello, DBD, LSR, LSU, LSAck*
LSAck, Hello, DBD, LSU, LSR
Hello, LSAck, LSU, LSR, DBD
Hello, DBD, LSR, LSU, LSAck*
LSAck, Hello, DBD, LSU, LSR
Hello, LSAck, LSU, LSR, DBD
7

Refer to the exhibit. If the IP addresses of the default gateway router and the DNS server are correct, what is the configuration problem?
The default-router and dns-server commands need to be configured with subnet masks.
The IP address of the default gateway router is not contained in the excluded address list.*
The IP address of the DNS server is not contained in the excluded address list.
The DNS server and the default gateway router should be in the same subnet.
The IP address of the default gateway router is not contained in the excluded address list.*
The IP address of the DNS server is not contained in the excluded address list.
The DNS server and the default gateway router should be in the same subnet.
8
A network administrator is testing IPv6 connectivity to a web server. The network administrator does not want any other host to connect to the web server except for the one test computer. Which type of IPv6 ACL could be used for this situation?
A network administrator is testing IPv6 connectivity to a web server. The network administrator does not want any other host to connect to the web server except for the one test computer. Which type of IPv6 ACL could be used for this situation?
a standard or extended ACL
only a named ACL*
only an extended ACL
an extended, named, or numbered ACL
only a standard ACL
only a named ACL*
only an extended ACL
an extended, named, or numbered ACL
only a standard ACL
9

Launch PT Hide and Save PT
Open the PT activity. Perform the tasks in the activity instructions and then answer the question.
To verify that the SVI is configured correctly, answer this question: Which ping command completed successfully?
Open the PT activity. Perform the tasks in the activity instructions and then answer the question.
To verify that the SVI is configured correctly, answer this question: Which ping command completed successfully?
ping 192.168.25.9*
ping 192.168.25.10
ping 192.168.25.7
ping 192.168.25.8
CONFIGURATION
ping 192.168.25.10
ping 192.168.25.7
ping 192.168.25.8
CONFIGURATION
SW0(config)#interface vlan 10
SW0(config-if)#ip address 192.168.63.2 255.255.255.0
SW0(config-if)#exit
SW0(config)#ip default-gateway 192.168.63.1
SW0(config)#end
SW0(config-if)#ip address 192.168.63.2 255.255.255.0
SW0(config-if)#exit
SW0(config)#ip default-gateway 192.168.63.1
SW0(config)#end
10
What is an advantage of using dynamic routing protocols instead of static routing?
What is an advantage of using dynamic routing protocols instead of static routing?
ability to actively search for new routes if the current path becomes unavailable*
fewer router resource overhead requirements
easier to implement
more secure in controlling routing updates
fewer router resource overhead requirements
easier to implement
more secure in controlling routing updates
11
How many classful networks are summarized by the static summary route ip route 192.168.32.0 255.255.248.0 S0/0/0?
How many classful networks are summarized by the static summary route ip route 192.168.32.0 255.255.248.0 S0/0/0?
16
4
2
8*
4
2
8*
12
Which switching method provides error-free data transmission?
Which switching method provides error-free data transmission?
fast-forward
fragment-free
store-and-forward*
integrity-checking
fragment-free
store-and-forward*
integrity-checking
13
A client is using SLAAC to obtain an IPv6 address for its interface. After an address has been generated and applied to the interface, what must the client do before it can begin to use this IPv6 address?
A client is using SLAAC to obtain an IPv6 address for its interface. After an address has been generated and applied to the interface, what must the client do before it can begin to use this IPv6 address?
It must send a DHCPv6 INFORMATION-REQUEST message to request the address of the DNS server.
It must send a DHCPv6 REQUEST message to the DHCPv6 server to request permission to use this address.
It must send an ICMPv6 Neighbor Solicitation message to ensure that the address is not already in use on the network.*
It must send an ICMPv6 Router Solicitation message to determine what default gateway it should use.
It must send a DHCPv6 REQUEST message to the DHCPv6 server to request permission to use this address.
It must send an ICMPv6 Neighbor Solicitation message to ensure that the address is not already in use on the network.*
It must send an ICMPv6 Router Solicitation message to determine what default gateway it should use.
14

Refer to the exhibit. Inter-VLAN communication between VLAN 10, VLAN 20, and VLAN 30 is not successful. What is the problem?
The switch interface FastEthernet0/1 is configured to not negotiate and should be configured to negotiate.
The switch interface FastEthernet0/1 is configured as an access interface and should be configured as a trunk interface.*
The access interfaces do not have IP addresses and each should be configured with an IP address.
The switch interfaces FastEthernet0/2, FastEthernet0/3, and FastEthernet0/4 are configured to not negotiate and should be configured to negotiate.
The switch interface FastEthernet0/1 is configured as an access interface and should be configured as a trunk interface.*
The access interfaces do not have IP addresses and each should be configured with an IP address.
The switch interfaces FastEthernet0/2, FastEthernet0/3, and FastEthernet0/4 are configured to not negotiate and should be configured to negotiate.
15
Which network design may be recommended for a small campus site that consists of a single building with a few users?
Which network design may be recommended for a small campus site that consists of a single building with a few users?
a network design where the access and core layers are collapsed into a single layer
a three-tier campus network design where the access, distribution, and core are all separate layers, each one with very specific functions
a collapsed core network design*
a network design where the access and distribution layers are collapsed into a single layer
a three-tier campus network design where the access, distribution, and core are all separate layers, each one with very specific functions
a collapsed core network design*
a network design where the access and distribution layers are collapsed into a single layer
16
How is the router ID for an OSPFv3 router determined?
How is the router ID for an OSPFv3 router determined?
the highest EUI-64 ID on an active interface
the highest IPv4 address on an active interface*
the highest IPv6 address on an active interface
the lowest MAC address on an active interface
the highest IPv4 address on an active interface*
the highest IPv6 address on an active interface
the lowest MAC address on an active interface
17
Refer to the exhibit. In the routing table entry, what is the administrative distance?
120*
12
2
24
12
2
24
18
What does an OSPF area contain?
What does an OSPF area contain?
routers that share the same router ID
routers whose SPF trees are identical
routers that share the same process ID
routers that have the same link-state information in their LSDBs*
routers whose SPF trees are identical
routers that share the same process ID
routers that have the same link-state information in their LSDBs*
19
Which command will create a static default route on R1 to send all traffic to the Internet and use serial 0/0 as the exit interface?
Which command will create a static default route on R1 to send all traffic to the Internet and use serial 0/0 as the exit interface?
R1(config)# ip route 255.255.255.255 0.0.0.0 serial 0/0
R1(config)# ip route 0.0.0.0 255.255.255.0 serial 0/0
R1(config)# ip route 0.0.0.0 255.255.255.255 serial 0/0
R1(config)# ip route 0.0.0.0 0.0.0.0 serial 0/0*
R1(config)# ip route 0.0.0.0 255.255.255.0 serial 0/0
R1(config)# ip route 0.0.0.0 255.255.255.255 serial 0/0
R1(config)# ip route 0.0.0.0 0.0.0.0 serial 0/0*
20
What is a result of connecting two or more switches together?
What is a result of connecting two or more switches together?
The number of collision domains is reduced.
The size of the broadcast domain is increased.*
The number of broadcast domains is increased.
The size of the collision domain is increased.
The size of the broadcast domain is increased.*
The number of broadcast domains is increased.
The size of the collision domain is increased.
21
Which DHCP IPv4 message contains the following information?
Which DHCP IPv4 message contains the following information?
Destination address: 255.255.255.255
Client IPv4 address: 0.0.0.0
Default gateway address: 0.0.0.0
Subnet mask: 0.0.0.0
Client IPv4 address: 0.0.0.0
Default gateway address: 0.0.0.0
Subnet mask: 0.0.0.0
DHCPDISCOVER*
DHCPACK
DHCPOFFER
DHCPREQUEST
DHCPACK
DHCPOFFER
DHCPREQUEST
22
What is meant by the term “best match” when applied to the routing table lookup process?
What is meant by the term “best match” when applied to the routing table lookup process?
exact match
longest match*
network match
supernet match
longest match*
network match
supernet match
23
Fill in the blank.
Using router-on-a-stick inter-VLAN routing, how many subinterfaces have to be configured to support 10 VLANs? ”10 ”
Fill in the blank.
Using router-on-a-stick inter-VLAN routing, how many subinterfaces have to be configured to support 10 VLANs? ”10 ”
24

Refer to the exhibit. The student on the H1 computer continues to launch an extended ping with expanded packets at the student on the H2 computer. The school network administrator wants to stop this behavior, but still allow both students access to web-based computer assignments. What would be the best plan for the network administrator?
Apply an inbound extended ACL on R1 Gi0/0.*
Apply an inbound standard ACL on R1 Gi0/0.
Apply an outbound extended ACL on R1 S0/0/1.
Apply an outbound standard ACL on R2 S0/0/1.
Apply an inbound extended ACL on R2 Gi0/1.
Apply an inbound standard ACL on R1 Gi0/0.
Apply an outbound extended ACL on R1 S0/0/1.
Apply an outbound standard ACL on R2 S0/0/1.
Apply an inbound extended ACL on R2 Gi0/1.
25

Refer to the exhibit. A network administrator is investigating a lag in network performance and issues the show interfaces fastethernet 0/0 command. Based on the output that is displayed, what two items should the administrator check next? (Choose two.)
electrical interference
duplex settings*
incorrect cable types
cable lengths*
damaged cable termination
duplex settings*
incorrect cable types
cable lengths*
damaged cable termination
26

Refer to the exhibit. A network administrator is configuring inter-VLAN routing on a network. For now, only one VLAN is being used, but more will be added soon. What is the missing parameter that is shown as the highlighted question mark in the graphic?
It identifies the number of hosts that are allowed on the interface.
It identifies the subinterface.
It identifies the native VLAN number.
It identifies the VLAN number.*
It identifies the type of encapsulation that is used.
It identifies the subinterface.
It identifies the native VLAN number.
It identifies the VLAN number.*
It identifies the type of encapsulation that is used.
27

Place the options in the following order:
hierarchical
modularity
resiliency
– not scored –
flexibility
28
Which command will verify the status of both the physical and the virtual interfaces on a switch?
Which command will verify the status of both the physical and the virtual interfaces on a switch?
show running-config
show vlan
show startup-config
show ip interface brief*
show vlan
show startup-config
show ip interface brief*
29

Refer to the exhibit. Which would be chosen as the router ID of R2?
The router ID has to be manually configured.*
2001:DB8:CAFE:2::/64
2001:DB8:CAFE:A001::/64
LLA: FE80::2
2001:DB8:CAFE:2::/64
2001:DB8:CAFE:A001::/64
LLA: FE80::2
30
A router with two LAN interfaces, two WAN interfaces, and one configured loopback interface is operating with OSPF as its routing protocol. What does the router OSPF process use to assign the router ID?
A router with two LAN interfaces, two WAN interfaces, and one configured loopback interface is operating with OSPF as its routing protocol. What does the router OSPF process use to assign the router ID?
the highest IP address that is configured on the WAN interfaces
the IP address of the interface that is configured with priority 0
the highest IP address on the LAN interfaces
the OSPF area ID that is configured on the interface with the highest IP address
the loopback interface IP address*
the IP address of the interface that is configured with priority 0
the highest IP address on the LAN interfaces
the OSPF area ID that is configured on the interface with the highest IP address
the loopback interface IP address*
31
Which two pieces of information are required when creating a standard access control list? (Choose two.)
Which two pieces of information are required when creating a standard access control list? (Choose two.)
subnet mask and wildcard mask
access list number between 100 and 199
source address and wildcard mask*
access list number between 1 and 99*
destination address and wildcard mask
access list number between 100 and 199
source address and wildcard mask*
access list number between 1 and 99*
destination address and wildcard mask
32
What is the effect of the access control list wildcard mask 0.0.0.15? (Choose two.)
What is the effect of the access control list wildcard mask 0.0.0.15? (Choose two.)
The first 28 bits of a supplied IP address will be ignored.
The first 28 bits of a supplied IP address will be matched.*
The first 32 bits of a supplied IP address will be matched.
The last four bits of a supplied IP address will be ignored.*
The last four bits of a supplied IP address will be matched.
The last five bits of a supplied IP address will be ignored.
The first 28 bits of a supplied IP address will be matched.*
The first 32 bits of a supplied IP address will be matched.
The last four bits of a supplied IP address will be ignored.*
The last four bits of a supplied IP address will be matched.
The last five bits of a supplied IP address will be ignored.
33
A college student is studying for the Cisco CCENT certification and is visualizing extended access lists. Which three keywords could immediately follow the keywords permit or deny as part of an extended access list? (Choose three.)
A college student is studying for the Cisco CCENT certification and is visualizing extended access lists. Which three keywords could immediately follow the keywords permit or deny as part of an extended access list? (Choose three.)
telnet
www
udp*
tcp*
ftp
icmp*
www
udp*
tcp*
ftp
icmp*
34
Which two keywords can be used in an access control list to replace a wildcard mask or address and wildcard mask pair? (Choose two.)
Which two keywords can be used in an access control list to replace a wildcard mask or address and wildcard mask pair? (Choose two.)
any*
some
gt
most
host*
all
some
gt
most
host*
all
35

Place the options in the following order:
Step 3
– target left blank –
Step 4
Step 2
Step 1
Step 3
– target left blank –
Step 4
Step 2
Step 1
36
Fill in the blank. Do not use abbreviations.
The “duplex full” command configures a switch port to operate in the full-duplex mode.
Fill in the blank. Do not use abbreviations.
The “duplex full” command configures a switch port to operate in the full-duplex mode.
37

Refer to the exhibit. R1 and R2 are OSPFv3 neighbors. Which address would R1 use as the next hop for packets that are destined for the Internet?
2001:DB8:ACAD:1::2
FE80::21E:BEFF:FEF4:5538*
2001:DB8:C5C0:1::2
FF02::5
FE80::21E:BEFF:FEF4:5538*
2001:DB8:C5C0:1::2
FF02::5
38
In a routing table which route can never be an ultimate route?
In a routing table which route can never be an ultimate route?
child route
level one route
parent route*
level two route
level one route
parent route*
level two route
39

Refer to the exhibit. Host A has sent a packet to host B. What will be the source MAC and IP addresses on the packet when it arrives at host B?
Source MAC: 00E0.FE10.17A3
Source IP: 10.1.1.10
Source IP: 10.1.1.10
Source MAC: 00E0.FE91.7799
Source IP: 10.1.1.1
Source IP: 10.1.1.1
Source MAC: 00E0.FE91.7799
Source IP: 192.168.1.1
Source IP: 192.168.1.1
Source MAC: 00E0.FE91.7799
Source IP: 10.1.1.10*
Source IP: 10.1.1.10*
Source MAC: 00E0.FE10.17A3
Source IP: 192.168.1.1
Source IP: 192.168.1.1
40
What is the effect of entering the network 192.168.10.1 0.0.0.0 area 0 command in router configuration mode?
What is the effect of entering the network 192.168.10.1 0.0.0.0 area 0 command in router configuration mode?
This command will have no effect because it uses a quad zero wildcard mask.
The interface with the IPv4 address 192.168.10.1 will be a passive interface.
OSPF advertisements will include the specific IPv4 address 192.168.10.1.
OSPF advertisements will include the network on the interface with the IPv4 address 192.168.10.1.*
The interface with the IPv4 address 192.168.10.1 will be a passive interface.
OSPF advertisements will include the specific IPv4 address 192.168.10.1.
OSPF advertisements will include the network on the interface with the IPv4 address 192.168.10.1.*
41
An administrator is trying to remove configurations from a switch. After using the command erase startup-config and reloading the switch, the administrator finds that VLANs 10 and 100 still exist on the switch. Why were these VLANs not removed?
An administrator is trying to remove configurations from a switch. After using the command erase startup-config and reloading the switch, the administrator finds that VLANs 10 and 100 still exist on the switch. Why were these VLANs not removed?
These VLANs cannot be deleted unless the switch is in VTP client mode.
These VLANs are default VLANs that cannot be removed.
These VLANs can only be removed from the switch by using the no vlan 10 and no vlan 100 commands.
Because these VLANs are stored in a file that is called vlan.dat that is located in flash memory, this file must be manually deleted.*
These VLANs are default VLANs that cannot be removed.
These VLANs can only be removed from the switch by using the no vlan 10 and no vlan 100 commands.
Because these VLANs are stored in a file that is called vlan.dat that is located in flash memory, this file must be manually deleted.*
42
What is a disadvantage when both sides of a communication use PAT?
What is a disadvantage when both sides of a communication use PAT?
Host IPv4 addressing is complicated.
End-to-end IPv4 traceability is lost.*
The flexibility of connections to the Internet is reduced.
The security of the communication is negatively impacted.
End-to-end IPv4 traceability is lost.*
The flexibility of connections to the Internet is reduced.
The security of the communication is negatively impacted.
43
What is associated with link-state routing protocols?
What is associated with link-state routing protocols?
shortest-path first calculations*
low processor overhead
split horizon
poison reverse
routing loops
low processor overhead
split horizon
poison reverse
routing loops
44

Refer to the exhibit. A PC at address 10.1.1.45 is unable to access the Internet. What is the most likely cause of the problem?
The NAT pool has been exhausted.*
Access-list 1 has not been configured properly.
The inside and outside interfaces have been configured backwards.
The wrong netmask was used on the NAT pool.
Access-list 1 has not been configured properly.
The inside and outside interfaces have been configured backwards.
The wrong netmask was used on the NAT pool.
45
In which type of attack does a malicious node request all available IP addresses in the address pool of a DHCP server in order to prevent legitimate hosts from obtaining network access?
In which type of attack does a malicious node request all available IP addresses in the address pool of a DHCP server in order to prevent legitimate hosts from obtaining network access?
CAM table overflow
DHCP snooping
MAC address flooding
DHCP starvation*
DHCP snooping
MAC address flooding
DHCP starvation*
46
When does a switch use frame filtering?
When does a switch use frame filtering?
The destination MAC address is for a host with no entry in the MAC address table.
The destination MAC address is for a host on a network supported by a different router.
The destination MAC address is for a host on a different network segment from the source of the traffic.
The destination MAC address is for a host on the same network segment as the source of the traffic.*
The destination MAC address is for a host on a network supported by a different router.
The destination MAC address is for a host on a different network segment from the source of the traffic.
The destination MAC address is for a host on the same network segment as the source of the traffic.*
47
How will a router handle static routing differently if Cisco Express Forwarding is disabled?
How will a router handle static routing differently if Cisco Express Forwarding is disabled?
Static routes that use an exit interface will be unnecessary.
It will not perform recursive lookups.
Ethernet multiaccess interfaces will require fully specified static routes to avoid routing inconsistencies.*
Serial point-to-point interfaces will require fully specified static routes to avoid routing inconsistencies.
It will not perform recursive lookups.
Ethernet multiaccess interfaces will require fully specified static routes to avoid routing inconsistencies.*
Serial point-to-point interfaces will require fully specified static routes to avoid routing inconsistencies.
48
An administrator created and applied an outbound Telnet extended ACL on a router to prevent router-initiated Telnet sessions. What is a consequence of this configuration?
An administrator created and applied an outbound Telnet extended ACL on a router to prevent router-initiated Telnet sessions. What is a consequence of this configuration?
The ACL will not work as desired because an outbound ACL cannot block router-initiated traffic.*
The ACL will work as long as it will be applied to all vty lines.
The ACL will work as desired as long as it is applied to the correct interface.
The ACL will not work because only standard ACLs can be applied to vty lines.
The ACL will work as long as it will be applied to all vty lines.
The ACL will work as desired as long as it is applied to the correct interface.
The ACL will not work because only standard ACLs can be applied to vty lines.
49
An administrator attempts to change the router ID on a router that is running OSPFv3 by changing the IPv4 address on the router loopback interface. Once the IPv4 address is changed, the administrator notes that the router ID did not change. What two actions can the administrator take so that the router will use the new IPv4 address as the router ID? (Choose two.)
An administrator attempts to change the router ID on a router that is running OSPFv3 by changing the IPv4 address on the router loopback interface. Once the IPv4 address is changed, the administrator notes that the router ID did not change. What two actions can the administrator take so that the router will use the new IPv4 address as the router ID? (Choose two.)
Reboot the router.*
Disable and re-enable IPv4 routing.
Shut down and re-enable the loopback interface.
Copy the running configuration to NVRAM.
Clear the IPv6 OSPF process.*
Disable and re-enable IPv4 routing.
Shut down and re-enable the loopback interface.
Copy the running configuration to NVRAM.
Clear the IPv6 OSPF process.*
50
When routing a large number of VLANs, what are two disadvantages of using the router-on-a-stick inter-VLAN routing method rather than the multilayer switch inter-VLAN routing method? (Choose two.)
When routing a large number of VLANs, what are two disadvantages of using the router-on-a-stick inter-VLAN routing method rather than the multilayer switch inter-VLAN routing method? (Choose two.)
Router-on-a-stick requires multiple physical interfaces on a router.
A dedicated router is required.*
Multiple subinterfaces may impact the traffic flow speed.*
Router-on-a-stick requires subinterfaces to be configured on the same subnets.
Multiple SVIs are needed.
A dedicated router is required.*
Multiple subinterfaces may impact the traffic flow speed.*
Router-on-a-stick requires subinterfaces to be configured on the same subnets.
Multiple SVIs are needed.



















